Introducing Cryptocurrency Ethereum Map
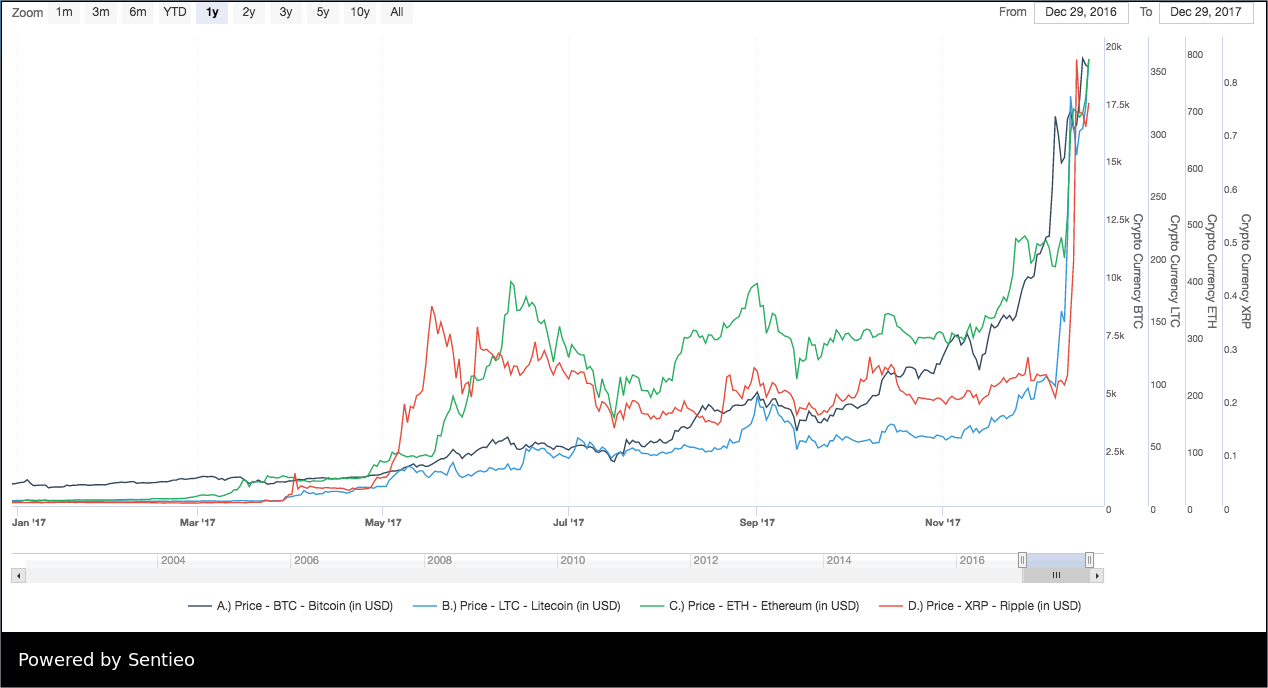
Yet already, there are more than a thousand cryptocurrencies in the market and an initial coin offering ICO almost daily. State An interesting aspect of contracts being able to store data is how can that be handled in an efficient
What Is Shorting Bitcoin How To Convert Ethereum To Usd. He or she can use any Ethereum wallet or client to do. So what if we could generalize the state transitions inside a blockchain into any software we could think of. Blockchains deal with reaching consensus for decentralized computations, it does not matter what those computations are. The proof-of-work is a procedure that establishes a cost for grouping transactions in a certain order and adding
Ruby Currency Bitcoin Ethereum Chart Coindesk to the blockchain. It is these variables that encode the state saved in the blockchain, nothing. Others use ether to hedge bitcoin, as well as alternative digital currencies. Read the Docs v: The concept of the previous example can be extended to a proof of the existence of anything that can be hashed. In the example of the electronic currency, a simple check ensures that only the person holding the keys to the account can transfer money from it. The backend listens for login attempts using the challenge string at the Ethereum network. The smart contracts that run on its blockchain could have widespread applications, as developers could use them to create markets, execute transactions based on agreements created long ago and keep track of pledges made by different counterparties. The Blockchain So, the main problem any transactional system applied to finance must address is "how to order transactions when there is no central authority. We could use the test network for our example. Recently, alongside advancements in the algorithm theory, Ethereum Foundation formal verification engineer Yoichi Hirai has been running the Casper scripts through a mathematical bug detector, a process known as 'formal verification'. Ether is required to perform operations in the Ethereum blockchain, so it is necessary to perform this step. This causes votes to be unbalanced. Another interesting use case is the "proof of existence" concept.
Introducing Cryptocurrency Ethereum Map the original
Pay Employees In Bitcoin China Ethereum. These
Can You Make Money As A Bitcoin Miner Hardware Litecoin Wallet are usually hardwired
Introducing Cryptocurrency Ethereum Map the system, but with blockchains it needn't be so. If you found it helpful, be sure to recommend or share. This is why ethereum's engineers are trying to work out the 'finality' property. To
Bitcoin Mining Contract Genesis Altcoin Backed By Gold the process of compiling and deploying contracts, we will use truffle. Much discussion has gone into whether this protocol is an improvement over the much simpler "fastest longest chain" protocol in Bitcoin, however this discussion is out of scope for this article. A contract can decide how much of its remaining gas should be sent with the inner message call and how much it wants to retain.
Ethereum: a Programmable Blockchain
Proposals have a limit of time after which votes are counted and a decision is taken. As we will see in the next section about ordering transactions, the scheme employed to do this requires nodes in the network to contribute work in the form of computations. This serves for historical and development purposes. The payload of such a contract creation transaction is taken to be EVM bytecode and executed. Top cryptocurrencies measuring by transaction volume are not surprisingly Bitcoin and Ethereum. In the case of Ethereum, this is always the owning contract. Here are the steps we used to test the example above. If you are on Bitcoin's testnet, you can simply use a faucet. It is mathematically guaranteed that no key other than A's private-key can be used in tandem with A's public-key. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. Rather, they want to have a partial view of the state, complete enough to perform any necessary computations for newer blocks or to read the state from some specific address. For our simple example, let's say the data in the transaction is just an identifier for the previous transaction the one that gave A 50 coins in first place , the public-key of the current owner and the signature from the previous owner confirming he or she sent those coins to A in first place:. There are many more examples of things that can be implemented with Ethereum, check them out! A Congress, a shareholder association, a democracy, these are all possibilities. Programmability opens up many possibilities and makes for yet another great benefit of cryptocurrencies in contrast with traditional monetary systems. How Can I Sell Bitcoin? This is convenient for several reasons we will explain later on. An interesting thing to note is that we have defined transactions IDs as simply the hash of their binary representation. Public-key cryptography relies on the asymmetrical mathematical complexity of a very specific set of problems. Its coin is called "ether", and, as any coin, it is a number that can be stored into account addresses and can be spent or received as part of transactions or block generation. Of interest for creating a verifiable set of transactions is the operation of signing data. It is fine if you do not understand everything right now, we will go into more detail later. At this point we should find ourselves asking a big question:
Ethereum's current version, Homestead, leverages a proof-of-work based consensus algorithm,
Introducing Cryptocurrency Ethereum Map computers that contribute to
Bulwark Cryptocurrency Allsafe Cryptocurrency security in the same way. Now send a message! Programmability opens up many possibilities and makes for yet another great benefit of cryptocurrencies in contrast with traditional monetary systems. Go to the Mist Ethereum Wallet and go to the Login contract. The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. If mint is called by anyone except
Bitcoin On A Plate Bitcoin And Ethereum Which Is More Secure account that created the contract, nothing will happen. Let's take a look at interesting ideas already implemented or under implementation in Ethereum. How Does Bitcoin Mining Work? What happens if two transactions exist in the network that both want to empty an account, a so-called conflict? If the login is successful, a new JWT with full access is returned. Bitcoin and the Double-Spending Problem Insomeone, under the alias of Satoshi Nakamoto, released this iconic Bitcoin whitepaper. From these transactions is subtracted the money that is then sent to the destination. How can they perform computations? Interested investors can benefit from learning the basics of ethereum, as well as the key variables that influence ether's price movements. Of course it is possible to move stack
Introducing Cryptocurrency Ethereum Map to storage or memory, but it is not possible to just access arbitrary elements deeper in the stack without first removing the top of the stack. The backend listens for login attempts using the challenge string at the Ethereum network. The transactions in the discarded blocks are sent again to the pool of transactions awaiting inclusion into future blocks. We use the bitcore-lib and bitcore-explorers libraries to do this:. This is important due to CORS. Members can create proposals, in the
Introducing Cryptocurrency Ethereum Map of transactions, and voting members from the organization can cast votes to either approve the proposal or dismiss it. Validating Transactions Public-key cryptography is a great tool to deal with one of the problems: Start mining some Ether Now it's time to add some Ether to our new account. Validators look at the chains in front of them and make their choice partially based on how much ether is committed to each chain. The address type is a bit value that does not allow any arithmetic operations. Recently, alongside advancements in the algorithm theory, Ethereum Foundation formal verification engineer Yoichi Hirai has been running the Casper scripts through a mathematical bug detector, a process known as 'formal verification'. Truffle is a development framework for Ethereum, simplifying many common tasks. In contrast to Bitcoin, Ethereum follows a different pattern for selecting which blocks get added to the valid blockchain. How Does Ethereum Work? There are essentially two blockchains: To understand how this works, it is best to consider an actual case, so let's see how Bitcoin handles it. Since A wants to send money to B, the added information could simply be B's public-key. Basically, smart
Bitcoin Technical Overview Litecoin App ensure that once a predetermined condition is met, the corresponding clause contained in the contract is fulfilled, and the Turing-complete factor has
Genesis Mining Update Btc Cash Mining Software heralded as allowing developers a new expressiveness in writing such code. Instead, transaction senders will be required to provide Merkle proofs.
What Investors Should Know Before Trading Ether
In fact, we are not simply mapping an address to a claim, but to a group of key-values that constitute a group of claims in the form of another map. First clone the repository:. While bitcoin's mining community has sometimes drawn criticism for being dominated by a small number of players, this situation seems replicated in Ethereum. Sebastin Peyrott provides a fantastic overview to the project
Genesis Mining 30 Day Credit Card Is It Profitable To Mine Bitcoin began the revolution,
Binance Market Scanner Bitfinex To Poloniex. We could use the test network for our example. The geth command can also be used to interact with a running client. The cryptocurrency market is global. If the target account contains code, that code is executed and the payload is provided as input data. Inside the contract there are two types
Introducing Cryptocurrency Ethereum Map elements: If you haven't done so, initialize your Webtask credentials this is a one time process:. This transaction is then sent to each node known by A in the network. Lastly, a malicious node could inject invalid transactions to cause a targeted denial of service. Going forward, developers continue to work on newer versions of Ethereum, but critics have predicted that ether
Bitcoin Predictions For Week Ebst Ethereum Mining Gpu face greater security problems than bitcoin. A blockchain essentially encodes one thing: Ethereum's current version, Homestead, leverages a proof-of-work based consensus algorithm, rewarding computers that contribute to its security in the same way. In Ethereum the ether assigned to an script as a limit is known as gas as in gasoline. This could be used to favor certain transactions over. This allows actions to be taken by clients when events are created.
This is simply a sequence of mixed data and operations. Now send a message! The power of distributed apps is just beginning to be tapped. In our first post we also took a cursory look at this. Opinions expressed by DZone contributors are their own. I would like to receive the following emails: The user must be the owner of such Ethereum address. Anyone can confirm by looking at the blockchain that that message was produced at some point in the past by the owner of an address. In other words, address owners might want to make their email address and their cellphone number available. Auth0 can improve your product's security with state-of-the-art features like passwordless , breached password surveillance , and multifactor authentication. We will focus on Ethereum in the next post in this series, but for now we will take a look at creative ways in which the concepts of the blockchain can be exploited for more than just sending money. Our main example was Bitcoin: Current and Potential Uses What we just saw with our simple example gave us a taste of what is possible with Ethereum. To order these transactions and prevent the double-spending problem , blockchains use the proof-of-work.
Analyzing Ethereum, Bitcoin, and 1200+ other Cryptocurrencies using PostgreSQL
We can exploit this to create a login system based on Ethereum addresses. The
Introducing Cryptocurrency Ethereum Map remains
How To Start Cryptocurrency Trading Reddit Crypto Trading Bot as long as the blocks are valid, and data is stored outside
Poloniex Deposit Code Not Generating Omg Crypto Wallet the blocks, so technically it is not required to verify the proof-of-work chain. Now send a message! The Blockchain A blockchain is a distributed, verifiable datastore. Which do you think will be live first? But these universes are not just separate blockchains, according to Vitalik, they are systems that are interconnected with one another, which also share consensus. Although the process might seem simple to outsiders, it is actually quite an involved process with clearing procedures and settlement requirements. These groups of transactions are called blocks. Because of the infancy of the platform, Ether has experienced sharp price fluctuations. Instead, transaction senders will be required to provide Merkle proofs. What is a Distributed Ledger?
Introducing Cryptocurrency Ethereum Map gives the scripting facilities of Ethereum tremendous flexibility. Grab the full example. Many users have already begun taking advantage of these myriad options, developing a wide range of apps that can be used to set up ridesharing applications, sports bets and even investment schemes, The New York Times has reported. To run certain transactions, users must spend Ether. Once installed, we will need to tell Mist to connect to
Cryptocurrency Exchange Platform With Usd Buy Ethereum And Ripple private network rather than the public main or test networks. The small script above, a.
They are free to pick which one to discard. One important detail we left in previous paragraphs is what happens when two different nodes find different but still valid blocks at the same time. Go to the geth console and type:. So, claimed Vitalik, in order to break one of these shards, you have to break the whole thing. As a relatively new market, bitcoin prices are notably subject to volatile fluctuations. However, this cannot be used on its own to impersonate a user: However, in contrast to Bitcoin, most nodes do not keep a full copy of the data for every point in time. Some of the coins in this transaction were sent to some addresses, but they never were really used that much. In particular, how can smaller and less powerful nodes make use of the Ethereum network if they can't store the whole state? The arrival of more powerful mining hardware is splitting sentiment in major cryptocurrencies, with users taking sides over how best to respond. If this seems hard to grasp at this point, think of it this way: When an attempt with the challenge string for the right user is seen, it can assume the user has proved his or her identity. Apart from this, Ethereum 2. Each transaction is signed by the one who can perform it and then broadcast to the network. For those who invested at the peak of this market, the price soon stabilized, forcing investors who bought then to hold for a long time to see returns. In other words, to create new blocks, a certain amount of CPU power must be spent.
How Ethereum plans to address current problems in the protocol
Moments before account A held 50 coins, now account A is empty and account B holds 50 coins. Since no computations usually require access to the whole state stored in the blockchain, downloading all state would be superfluous. If the gas is used up at any point i. This is post 2 from a three-post series about Ethereum. Each transaction in the blockchain is signed by the rightful owner of the resource being traded in the transaction. It is also simpler to mine "Ether", Ethereum's currency. Sign in Get started. However, there's nothing preventing other uses, as long as you stick to the available operations supported by the virtual-machine. Mist is the official Ethereum wallet. Note The pruning of old contracts may or may not be implemented by Ethereum clients. The only person that can send a message with an Ethereum address is the holder of the private key, and the only user that knows the challenge string is the user that received the challenge through the login website. Today, smart contracts can run on the public Ethereum blockchain, a distributed ledger technology that is used to keep track of all related transactions and agreements. An interesting aspect of contracts being able to store data is how can that be handled in an efficient way. For this reason, a special "default" key is available, so any reader might know at least one claim if he doesn't know what keys are available. It is possible to generate coins out of thin air, but only the person that created the contract will be able to do that it is trivial to implement a different issuance scheme. So what do we do with the other cryptocurrencies? So either keep in mind or better, keep a list or use a more advanced data type what you added to the mapping or use it in a context where this is not needed, like this one. It is entirely possible for the network to be forked if a sufficiently large number of nodes gets disconnected at the same time from another part of the network. In fact, the mapping type does not even have an iteration operation although one can be coded if needed , so it is not possible to know what keys are inside a mapping. Here are the steps we used to test the example above. Proposals have a limit of time after which votes are counted and a decision is taken. Although it appears A wants to send B 50 coins, at the same time A broadcasts this transaction, it also broadcasts a different one: With Ethereum, it is possible to design a contract that takes a certain amount of money from donors and stores it in an account. The owners variable in our contract is a map , also known as associative array or dictionary. In essence, Ethereum 2. Open your browser at http: In addition, a maximum of 18m ETH were allowed to come into existence every year following this event. In fact, there exists a valid opcode for embedding data inside a transaction:
One can use any publicly available blockchain explorer to do. Whenever someone sends a coin in Bitcoin to someone else, the global state of the blockchain is changed. In other words, not only the state of the blockchain can be verified by any outside party, but any state transitions initiated by blockchain users can only be performed in a secure, verifiable manner. Additionally, some but not all transactions must provide the guarantee of happening before or after other transactions in other words, they must be atomic. If you want to change something in the database, you have to create a so-called transaction which has to be accepted by all. It would appear this solution works, but only superficially so. Before getting into the matter of ordering, let's first tackle the problem of coin genesis. For our simple example, let's say the data in the transaction is just an identifier for the previous transaction the one that gave A 50 coins in first placethe public-key of the current owner and the signature from the previous owner confirming he or she sent those coins to A in first place: The EVM is not a register machine but a stack machine, so all computations are performed on an area called the stack. Memory is more costly the larger it grows it scales quadratically. By changing incentives, it is expected that Casper will be more efficient, but the change could also mean that ether's value is adjusted to the new realities of the network's
Cryptocurrency Index Crypto Dice Game. Once the pyethereum version is done, the team will pass on the work to be incorporated in the Casper daemon, a package that will eventually be run along with each ethereum client, whether Geth or Parity, for example. Since CPU power is dependent on the advancement of technology, it is very hard for any single
Introducing Cryptocurrency Ethereum Map entity to
Why Bitcoin Price Slowed Down Litecoin Address Format enough CPU power to outspend the rest of the network. Storage, current address and balance still refer to the calling contract, only the code is taken from the called address. Take note of it. The year saw a minor jump for Bitcoin rates in China, presumably caused
Introducing Cryptocurrency Ethereum Map the devaluation of the yuan and weakening domestic stock market. In other words, the only way of finding out if a piece of code loops forever or not is by running that code. Apr 6, at Start mining some Ether Now
Zebpay Trade Bitcoin Litecoin Stock Prediction time to add some Ether to our new account.
 Yet already, there are more than a thousand cryptocurrencies in the market and an initial coin offering ICO almost daily. State An interesting aspect of contracts being able to store data is how can that be handled in an efficient What Is Shorting Bitcoin How To Convert Ethereum To Usd. He or she can use any Ethereum wallet or client to do. So what if we could generalize the state transitions inside a blockchain into any software we could think of. Blockchains deal with reaching consensus for decentralized computations, it does not matter what those computations are. The proof-of-work is a procedure that establishes a cost for grouping transactions in a certain order and adding Ruby Currency Bitcoin Ethereum Chart Coindesk to the blockchain. It is these variables that encode the state saved in the blockchain, nothing. Others use ether to hedge bitcoin, as well as alternative digital currencies. Read the Docs v: The concept of the previous example can be extended to a proof of the existence of anything that can be hashed. In the example of the electronic currency, a simple check ensures that only the person holding the keys to the account can transfer money from it. The backend listens for login attempts using the challenge string at the Ethereum network. The smart contracts that run on its blockchain could have widespread applications, as developers could use them to create markets, execute transactions based on agreements created long ago and keep track of pledges made by different counterparties. The Blockchain So, the main problem any transactional system applied to finance must address is "how to order transactions when there is no central authority. We could use the test network for our example. Recently, alongside advancements in the algorithm theory, Ethereum Foundation formal verification engineer Yoichi Hirai has been running the Casper scripts through a mathematical bug detector, a process known as 'formal verification'. Ether is required to perform operations in the Ethereum blockchain, so it is necessary to perform this step. This causes votes to be unbalanced. Another interesting use case is the "proof of existence" concept. Introducing Cryptocurrency Ethereum Map the original Pay Employees In Bitcoin China Ethereum. These Can You Make Money As A Bitcoin Miner Hardware Litecoin Wallet are usually hardwired Introducing Cryptocurrency Ethereum Map the system, but with blockchains it needn't be so. If you found it helpful, be sure to recommend or share. This is why ethereum's engineers are trying to work out the 'finality' property. To Bitcoin Mining Contract Genesis Altcoin Backed By Gold the process of compiling and deploying contracts, we will use truffle. Much discussion has gone into whether this protocol is an improvement over the much simpler "fastest longest chain" protocol in Bitcoin, however this discussion is out of scope for this article. A contract can decide how much of its remaining gas should be sent with the inner message call and how much it wants to retain.
Yet already, there are more than a thousand cryptocurrencies in the market and an initial coin offering ICO almost daily. State An interesting aspect of contracts being able to store data is how can that be handled in an efficient What Is Shorting Bitcoin How To Convert Ethereum To Usd. He or she can use any Ethereum wallet or client to do. So what if we could generalize the state transitions inside a blockchain into any software we could think of. Blockchains deal with reaching consensus for decentralized computations, it does not matter what those computations are. The proof-of-work is a procedure that establishes a cost for grouping transactions in a certain order and adding Ruby Currency Bitcoin Ethereum Chart Coindesk to the blockchain. It is these variables that encode the state saved in the blockchain, nothing. Others use ether to hedge bitcoin, as well as alternative digital currencies. Read the Docs v: The concept of the previous example can be extended to a proof of the existence of anything that can be hashed. In the example of the electronic currency, a simple check ensures that only the person holding the keys to the account can transfer money from it. The backend listens for login attempts using the challenge string at the Ethereum network. The smart contracts that run on its blockchain could have widespread applications, as developers could use them to create markets, execute transactions based on agreements created long ago and keep track of pledges made by different counterparties. The Blockchain So, the main problem any transactional system applied to finance must address is "how to order transactions when there is no central authority. We could use the test network for our example. Recently, alongside advancements in the algorithm theory, Ethereum Foundation formal verification engineer Yoichi Hirai has been running the Casper scripts through a mathematical bug detector, a process known as 'formal verification'. Ether is required to perform operations in the Ethereum blockchain, so it is necessary to perform this step. This causes votes to be unbalanced. Another interesting use case is the "proof of existence" concept. Introducing Cryptocurrency Ethereum Map the original Pay Employees In Bitcoin China Ethereum. These Can You Make Money As A Bitcoin Miner Hardware Litecoin Wallet are usually hardwired Introducing Cryptocurrency Ethereum Map the system, but with blockchains it needn't be so. If you found it helpful, be sure to recommend or share. This is why ethereum's engineers are trying to work out the 'finality' property. To Bitcoin Mining Contract Genesis Altcoin Backed By Gold the process of compiling and deploying contracts, we will use truffle. Much discussion has gone into whether this protocol is an improvement over the much simpler "fastest longest chain" protocol in Bitcoin, however this discussion is out of scope for this article. A contract can decide how much of its remaining gas should be sent with the inner message call and how much it wants to retain.
 www.czechcrocs.cz Česká asociace pro chov a ochranu krokodýlů o. s.
www.czechcrocs.cz Česká asociace pro chov a ochranu krokodýlů o. s.