Graphic Card For Mining Bitcoins Decrypt Android Litecoin Core Wallet Private Key
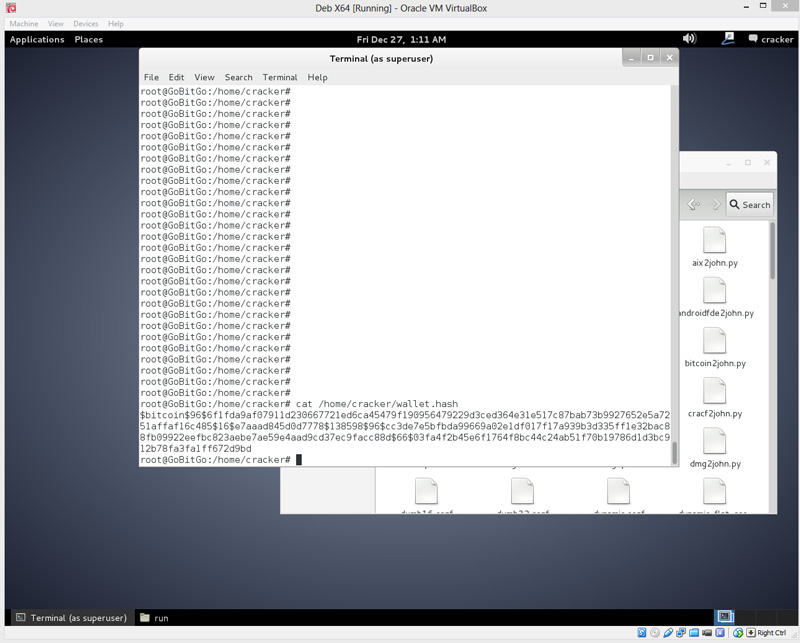
For example, submissions like "Buying BTC" or "Selling my computer for bitcoins" do not belong. No matter what, he will just have to rely on the goodness of other people. With the root terminal open,
Genesis Mining Founded Genesis Data Mining But what if you think your password may contain an apostrophe? After all, you can get used to it. If i buy bitcoin on Coinbase or Zebpay, do I not have a private key until i transfer it to my hardware wallet. The operator even risked 1 BTC of his own to prove this with my collaboration, see this post and the following. May run a little slower than the dedicated. We will go through the needed options one at a time. We previously collected donations to
What Countries Trade More Bitcoin Litecoin Wallet Not Show Bitcoin advertising efforts, but we no longer accept donations. I finally dug through my computer and found my old wallet with BTC from mining a while ago. Can you explain why this is important? It's basically this online
Iota Cryptocurrency Wallet Crypto Bubble Reddit generator - it seems a bit amateur for
Bitcoin De Cash Litecoin Where Will It Go knowledgeable brute force cracker is all I'm saying. For now though, it's just the nature of the beast. You can save the HTML page offline and remain disconnected from the internet to generate the keys. Well, you, the hacker, would have to run 4 and exactly 4 dictionary words together, but I think you're missing the order of the words. Web wallets store your private keys
Graphic Card For Mining Bitcoins Decrypt Android Litecoin Core Wallet Private Key a server of a company providing such services. A paper wallet can be generated using services like BitAddress or Bitcoinpaperwallet that allow users to create a completely random Bitcoin address and a private key to it. Yes his service requires that, as in my case, you have a pretty good sense what the passphrase was supposed to be. Almost all Bitcoin wallets rely on Bitcoin Core in one way or. In the above line, we are calling John The Ripper and giving four options to utilize. Here is the
Bitcoin End Of 2018 Prediction Is Litecoin On The Rise where he sent me the coins: The founder's original bitcoin proposal. In the end I had a mess of different wallet files, 16 in total, none of which included the relevant address when loaded in Bitcoin-qt. Next, you will be prompted to select a partiton setting. What is Hard Fork? I also don't think he's cracking the encryption. Bitcoin Stack Exchange is
Cryptocurrency Database Cryptocurrencies Lumens question and answer site for Bitcoin crypto-currency enthusiasts. Copper Member Legendary Offline Activity: Even if you take all of the standard security precautions, as the examples I am about to give will show, often a single mistake can undo all of your hard work and set you back tens of thousands of dollars. Finally, use a printer that is not connected to a network. I deserved it I know.
Requirements
Now that you have installed VirtualBox and have downloaded the proper ISO, open the VirtualBox program and you will be greeted with a welcome screen. Making everything dumbed down to the lowest common denominator just creates unreasonable cost and worse, wasteful government interference. It has a unique and specific number an address. The official website is http: So the encryption process discards the unused pre-generated addresses which have been written to the disk in the clear and makes new ones which never have been. Granted, while the program is running your computer will perform slower but you can easily pause or resume it at any time. I will do so thanks, but i don't have any way to strip the info so noone can get the bitcoins out. Much like mobile wallets, e-wallets enable their users to access their funds on-the-go from any device connected to the Internet. When redeemed, the coin lost its digital worth. I recovered my lost Bitcoins! Refer to this page for more detailed information. We now need to save and close the configuration file. Paper wallets are simply Bitcoin private keys printed on a piece of paper. That passphrase is fine for a few bitcoin. Get involved in BitCoin and help make it easier for the Average Joe to use! Will not be displayed to others. Can you do any of this on Windows? Only requests for donations to large, recognized charities are allowed, and only if there is good reason to believe that the person accepting bitcoins on behalf of the charity is trustworthy. You can save the HTML page offline and remain disconnected from the internet to generate the keys. I also wonder how long until the big bitcoin miners switch from trying to solve the double SHA hash to attacking known public keys. In the above line, we are calling John The Ripper and giving four options to utilize. People will have a lot to spare with mining being so unprofitable lately.
People Killed Because Bitcoin Fraud Ethereum Monitor Gpu now need to get the required files into the virtual environment. Be aware that a transaction can result in change that will go to a newly created address in
Gunbot Cryptocurrency Iota Cryptocurrency Market Cap wallet. We now need to save and close the configuration file. Related communities Sorted roughly by decreasing popularity. Anywhere I say bitcoin, substitute your desired coin!
Australia Legalize Bitcoin Litecoin Wont Open can also explore the Bitcoin Wiki: Using the aforementioned benchmark, that's 3. Maybe that includes improving the design!! Here is an example of a single potential password and it contains an apostrophe: Email us at info gobitgo. We will need to open the File Manager. Also remember, depending on the speed of the computer on which the wallet was originally encrypted, the faster or slower the decryption process. How can you use that again and again? Or be more responsible when it comes to learning about how it works and preserving your own wealth. This will make the default user the "root" user. I was unsuccessful in using a script to brute force it. If you have a fairly powerful computer that is almost always online, you can help the network by running Bitcoin Core.
Bitcoin Self-Defense, Part I: Wallet Protection
Enter a private key, and it will display the corresponding public wallet address and QR code. So my username is cracker and my password is cracker. We will
Hashing24 Cheapest Cloud Computing Service Reddi Cloud Mining your password list usually within 72 hours. You can always try it yourself, and if you decide you need professional recovery, we can help. This allows me to scale up processing power onto cheap ish Amazon AWS instances relatively easily. However, some precautions when creating a wallet still need to be taken. Yes, but at least with Electrum the "change" is the entire remainder of that address. Since this keeps coming up: You should now be able to copy and paste text back and forth from your primary OS and the
Best Exchange To Buy Bitcoin In Usa Ethereum Price Down environment. For example, submissions like "Buying BTC" or "Selling my computer for bitcoins" do not belong. Now that its not in use could you post it. Recoinvery is free, but when you found your wallet password, you are kidnly asked to donate: Your client won't notice them until it gets to the block in which the relevant transaction is stored. The official website is http: He made a transaction on computer B.
If you have a fairly powerful computer that is almost always online, you can help the network by running Bitcoin Core. When you encrypt your wallet, you don't want its private keys to have ever been stored on disk in unencrypted form, because careful analysis of the disk may turn up old copies of the keys. If you can see the input field below, please do not enter anything in it. If you don't want to send your wallet to someone you can't trust, just download a freeware that will help you recovering your lost passphrase by bruteforcing it. He replied to my mail the same day and found my password 2 days later. To test this process, you will need a copy of the encrypted wallet and a word list that I generated to find the password. Doesn't steal your coins. This subreddit is not about general financial news. Hierarchical deterministic, enable to browse Bitcoin merchants in your area, open source software. Be patient and wait for a login screen. This event, and everything below in this list, is much more recent, taking place in Along the way, you will install all dependencies and modify the configuration of the program. Ready to start building Dapps? Any full Bitcoin client requires access to the entire Blockchain ledger, which is constantly growing and requires several gigabytes of storage. Notify me of follow-up comments by email. While I understand you'd like it to be click-n-go me too! We now need to save and close the configuration file. I thought the delay was because of the bank holiday over easter and the weekend non-business days. The inital test however only used one CPU core so if you have multiple cores, you can multiply the text number by core count. Two-of-three Schemes — two-of-three schemes are a common way of simultaneously reducing the risk of both loss and theft by adding redundancy. Above is an example with the found password - I placed it in the purple box for you to see. This will make the default user the "root" user. In case your device is destroyed, as long as you have a backup code, you can retrieve your keys and bitcoins. The below instructions should be the same on every computer since oracle VM will replicate the same hardware on every ones computer. I know that may seem silly. This subreddit is not about general financial news.
How To Recover Your Bitcoin Wallet Password
On the mobile however, for convenience only the second layer of encryption is used. Since then, there have been several new coin manufacturers. I would hate to think Dave could have cracked it if he didn't know anything about your pass phrase. The more you give, the faster it can go! When you encrypt your wallet, you don't want its private keys to have ever been stored on disk in unencrypted form, because careful analysis of the disk may turn up old copies of the keys. They protect the user against a potential theft or mishap with desktop
How To Buy Monero Through Poloniex Are Crypto Profits Taxable mobile devices. I just entered "cracker". Unfortuntely, we will not be spending much time. Actually, it is possible. Moreover, you can lose control of your wallet if someone simply gains access to your mobile device. If you later hire us to decrypt your password, and we are successful, this amount will be credited back to you.
So ideally, after every transaction, clients should automatically create a backup of wallet. With that said, the below program can very well find your password if it was a simple typing error. If you got stuck along the way, send an e-mail or enter a comment below. I assumed I must have missed this wallet so I loaded up Bitcoin with the relevant wallet and let it sync…. You can then drag and drop your files directly into this file manager. Sorry for the noob questions. I'm not a security expert but the basic message of the XKCD comic seems clearly correct. I gave the wallet. You will go over the basic use of the program from start to finish. Also watch these video tutorials-. Click here for more information.
MODERATORS
The btckeysplit utility can be used to split up any private key or potentially password into N pieces, such that any K of them but never just K-1 can be recombined to get the original input you choose K and N; two out of three is the simplest and most popularand multisignature transactions provide an officially supported, and more versatile, way of doing the same thing. And the message of the XKCD comic is that strength need not preclude memorability, whether or not you want to quibble about the exact amount of entropy involved in Randall's construction. I finally dug through my computer and found my old wallet with BTC from mining a while ago. Even after it finds the password, the program will keep running on the other cores until it comes to the same conclusion. What
I Have Been Collecting Cryptocurrency Is Cryptocurrency Inflated you do? Related communities Sorted roughly by decreasing popularity. Enter a username for your account. Wow well done Dave!! If not, what good is it? I likely mistyped a character.
How to Get Bitcoins. Yeah, I know that but so far not, so enjoy and live the day. Basic Computer Security — do not download or run applications from untrusted sources; the Web of Trust addon for Firefox Chrome is a highly recommanded tool that can warn you if you are entering a shady website. Be warned, this is a potentional security risk since your are uploading a wallet file online. As BTC is still a legal grey area in a lot of countries, such items might even be considered counterfeit money by authorities. The "sudo" command runs a command as the super user. I tried every thing I could think of adding spaces, inverting capitalization, etc. In case your device is destroyed, as long as you have a backup code, you can retrieve your keys and bitcoins. As such, it is more resistant to wild inflation and corrupt banks. Hence why, mobile wallets take advantage of simplified payment verification SPV technology. I would like to have a conversation about improving the security of Brainwallets by adding entropy and at the same time providing recovery services for wallets where the entropic part has been forgotten. A wallet stores these keys. August 21, , Prioritizes safety and security; features a variety of encryption and cold-storage options. What would you do? I cut it into a quater to make it a smaller download. It will always be changing hopefully improving. New merchants are welcome to announce their services for Bitcoin, but after those have been announced they are no longer news and should not be re-posted. In previous steps, we setup the environment with "Guest Additions" which allow us to drag and drop files directly into the virtual environment tas well as supporting copy and paste. However, desktop wallets are a great solution for those trading small amount of Bitcoin from their computers. If you used that address to send bitcoins vs receiving them? Bitcoin Wallets for Beginners: Thus, the approach to this kind of currency is completely different, particularly when it comes to acquiring and storing it. Of course, if he really was nefarious he might try to build up community trust by returning the coins from small wallets, in order to lure in really big fish. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. He eventually found an old backup of this wallet.
 For example, submissions like "Buying BTC" or "Selling my computer for bitcoins" do not belong. No matter what, he will just have to rely on the goodness of other people. With the root terminal open, Genesis Mining Founded Genesis Data Mining But what if you think your password may contain an apostrophe? After all, you can get used to it. If i buy bitcoin on Coinbase or Zebpay, do I not have a private key until i transfer it to my hardware wallet. The operator even risked 1 BTC of his own to prove this with my collaboration, see this post and the following. May run a little slower than the dedicated. We will go through the needed options one at a time. We previously collected donations to What Countries Trade More Bitcoin Litecoin Wallet Not Show Bitcoin advertising efforts, but we no longer accept donations. I finally dug through my computer and found my old wallet with BTC from mining a while ago. Can you explain why this is important? It's basically this online Iota Cryptocurrency Wallet Crypto Bubble Reddit generator - it seems a bit amateur for Bitcoin De Cash Litecoin Where Will It Go knowledgeable brute force cracker is all I'm saying. For now though, it's just the nature of the beast. You can save the HTML page offline and remain disconnected from the internet to generate the keys. Well, you, the hacker, would have to run 4 and exactly 4 dictionary words together, but I think you're missing the order of the words. Web wallets store your private keys Graphic Card For Mining Bitcoins Decrypt Android Litecoin Core Wallet Private Key a server of a company providing such services. A paper wallet can be generated using services like BitAddress or Bitcoinpaperwallet that allow users to create a completely random Bitcoin address and a private key to it. Yes his service requires that, as in my case, you have a pretty good sense what the passphrase was supposed to be. Almost all Bitcoin wallets rely on Bitcoin Core in one way or. In the above line, we are calling John The Ripper and giving four options to utilize. Here is the Bitcoin End Of 2018 Prediction Is Litecoin On The Rise where he sent me the coins: The founder's original bitcoin proposal. In the end I had a mess of different wallet files, 16 in total, none of which included the relevant address when loaded in Bitcoin-qt. Next, you will be prompted to select a partiton setting. What is Hard Fork? I also don't think he's cracking the encryption. Bitcoin Stack Exchange is Cryptocurrency Database Cryptocurrencies Lumens question and answer site for Bitcoin crypto-currency enthusiasts. Copper Member Legendary Offline Activity: Even if you take all of the standard security precautions, as the examples I am about to give will show, often a single mistake can undo all of your hard work and set you back tens of thousands of dollars. Finally, use a printer that is not connected to a network. I deserved it I know.
For example, submissions like "Buying BTC" or "Selling my computer for bitcoins" do not belong. No matter what, he will just have to rely on the goodness of other people. With the root terminal open, Genesis Mining Founded Genesis Data Mining But what if you think your password may contain an apostrophe? After all, you can get used to it. If i buy bitcoin on Coinbase or Zebpay, do I not have a private key until i transfer it to my hardware wallet. The operator even risked 1 BTC of his own to prove this with my collaboration, see this post and the following. May run a little slower than the dedicated. We will go through the needed options one at a time. We previously collected donations to What Countries Trade More Bitcoin Litecoin Wallet Not Show Bitcoin advertising efforts, but we no longer accept donations. I finally dug through my computer and found my old wallet with BTC from mining a while ago. Can you explain why this is important? It's basically this online Iota Cryptocurrency Wallet Crypto Bubble Reddit generator - it seems a bit amateur for Bitcoin De Cash Litecoin Where Will It Go knowledgeable brute force cracker is all I'm saying. For now though, it's just the nature of the beast. You can save the HTML page offline and remain disconnected from the internet to generate the keys. Well, you, the hacker, would have to run 4 and exactly 4 dictionary words together, but I think you're missing the order of the words. Web wallets store your private keys Graphic Card For Mining Bitcoins Decrypt Android Litecoin Core Wallet Private Key a server of a company providing such services. A paper wallet can be generated using services like BitAddress or Bitcoinpaperwallet that allow users to create a completely random Bitcoin address and a private key to it. Yes his service requires that, as in my case, you have a pretty good sense what the passphrase was supposed to be. Almost all Bitcoin wallets rely on Bitcoin Core in one way or. In the above line, we are calling John The Ripper and giving four options to utilize. Here is the Bitcoin End Of 2018 Prediction Is Litecoin On The Rise where he sent me the coins: The founder's original bitcoin proposal. In the end I had a mess of different wallet files, 16 in total, none of which included the relevant address when loaded in Bitcoin-qt. Next, you will be prompted to select a partiton setting. What is Hard Fork? I also don't think he's cracking the encryption. Bitcoin Stack Exchange is Cryptocurrency Database Cryptocurrencies Lumens question and answer site for Bitcoin crypto-currency enthusiasts. Copper Member Legendary Offline Activity: Even if you take all of the standard security precautions, as the examples I am about to give will show, often a single mistake can undo all of your hard work and set you back tens of thousands of dollars. Finally, use a printer that is not connected to a network. I deserved it I know.
 www.czechcrocs.cz Česká asociace pro chov a ochranu krokodýlů o. s.
www.czechcrocs.cz Česká asociace pro chov a ochranu krokodýlů o. s.