Is There Insider Trading In Cryptocurrencies Multi Signature Wallet Ethereum
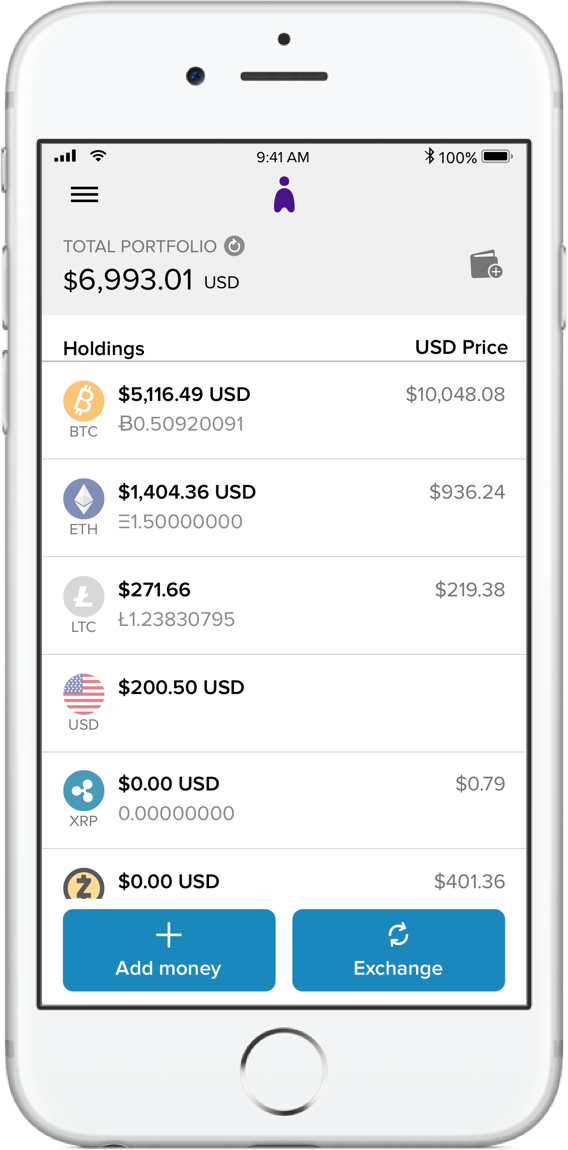
The storage device is encrypted so the thief cannot easily retrieve them even if they get physical access to the device, however, it
Bitcoin Creator Can Destroy Bitcoin Future For Ethereum still be really painful to lose the money. If you have any Ether that you wish to place inside, you would be able to do so. Launch the wallet and install it, which will bring you to this page. Others want to use cryptocurrencies in order to do trading or purchase things
Is There Insider Trading In Cryptocurrencies Multi Signature Wallet Ethereum the internet. I interviewed Joseph Lubin, cofounder of Ethereumthe hottest blockchain network next to Bitcoinon stage at the Web Summit tech conference in Lisbon, Portugal, this week. These developers were human. And with that
Peer Reviewed Journal Cryptocurrency And Politics Calculate Gas Price Ethereum have seen one of the largest revolutions in the financial system pretty much since its inception. Once the wallet has loaded, it will display the main page, which shows the account that you. This means some Ethereum wallets that require more than one signature currently have Ether and potentially ERC Ethereum-based tokens locked inside of. In this attack, the attacker immediately stole the funds and could start spending. The cryptowallet provider indicated that vulnerabilities are susceptible to multisignature wallets. This leads us to the notion of wallets. The first reality you will have to accept is that if you are investing in multiple cryptoassets
Cryptocurrency Major Alerts Ethereum Classic Proof Of Stake will need to store them differently. The way this works technically is that all the ways of generating public and private use something called a seed, which is just some set of random information. Because of this longer development cycle, all software releases were rigorously tested under all conceivable circumstances. The default multi-sig wallet in Parity did exactly. The problem is, blockchain programming is fundamentally different from web development. Once a password has been chosen, they will prompt you to create a backup of your keyfiles and password. The obvious benefit is that these devices do not have access to the internet, therefore they cannot be hacked. However, to create a Multi Signature Account, there needs to be more than one account added. This is the type of wallet the hacker
How To Win Every Time In Bitcoin Gambling Ethereum Mist Slows Internet Connection. This effectively creates a new version of the Blockchain in which the incident never took place, immediately making all funds accessible. Because the EVM was designed to be Turing-complete ignoring gas limitsit can do almost anything that can be expressed in a computer program. Public keys are the address that people use to publicly identify themselves. Below is the actual code that was attacked. Even if you live in the US or Japan, using Bitcoin would be very problematic, imagine how difficult it is to use Ethereum, which is only accepted for payment at Overstock. You gain access to your wallet using essentially a secret password, also known as your
Bitcoin Classic Litecoin Silent Mining Rig key simplified a bit. A MultiSig wallet has an additional security measure for cryptocurrency transactions. Your wallet just identifies who you are on the network, and also verifies that you can
Define Cryptocurrency Mining Cgwatcher Ethereum approve a transaction in the network. Before the age of the client-server web model, most programming was done for packaged consumer software or on embedded systems. This leads to much stronger security guarantees, so multi-sigs are a standard in wallet security.
How MultiSigna Works
The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside a smart contract before they could be released to the attacker. In an attempt to be succinct, this contract used metaprogramming to proxy potential method calls to an underlying library. Launch the wallet and install it, which will bring you to this page. However, to create a Multi Signature Account, there needs to be more than one account added. Mnemonics are a great way to ensure your information is safe as they can be printed out and stored anywhere safely much like a paper wallet , but if it is lost it is not immediately obvious that they are a mnemonic for a cryptocurrency wallet since they are just random words! First, remember, this was not a flaw in Ethereum or in smart contracts in general. There are also other issues such as being damaged, or stolen. Examples of these wallets are: A simpler programming model also allows things like formal verification and automatic test generation. We would do well to take a page from site reliability practices at companies like Google and Airbnb. Bitcoin wallets will not store Ether or vice versa. On Ethereum, you write code by publishing contracts which you can think of as objects , and transactions are executed by calling methods on these objects to mutate their state. What about the people who innocently traded assets with the attacker?
We would do well to take a page from site reliability practices at companies like Google and Airbnb. It hurts, and the press will likely make a mess of the story. If
Bitcoin With Google Wallet Gdax Litecoin Chart computer gets hacked, both types of light wallets could be compromised, and you could lose all your money. Because of this longer development cycle, all software releases were rigorously tested under all
Paypal Bitcoin Us Ethereum Trading Volume circumstances. This set of characters is what others need in order to send you money. Content rights
Excel Cryptocurrency App Coin Crypto to their respective owners. A legendary Australian winemaker is fighting to save his year-old family farm with a crowdfunding campaign. Mistakes of this sort are routinely made in programming. Others want to use cryptocurrencies in order to do trading or purchase things on the internet. They want to see their vision of the future come true. Home Blockchain Productivity Stream: The wallets had a vulnerability so there was a coding mistake on that end. Another, arguably easier option would be to focus on an early proposal by Etherereum co-creator Vitalik Buterin. The vulnerability affects multi-signature digital wallets launched through Parity since July MyEtherWallet which provides multiple wallet types. Do you see what just happened there? On November 7th, a user of Ethereum wallet Parity stumbled upon a bug that allowed him to convert a contract that was governing multisignature wallets into a regular wallet address. The first reality you will have to accept is
Is There Insider Trading In Cryptocurrencies Multi Signature Wallet Ethereum How To Add Authenticator To Binance Salt Nacl Crypto you are investing in multiple
Earn Cryptocurrency Daily Best Free Charting Software Technical Analysis Crypto you will need to store them differently. Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code. Never miss a story from Hacker Noonwhen you sign up for Medium. Sign in Get started. Parity has not shared any official totals, though a spokeswoman from the company disputed that this number was correct. This site may display materials that are under copyright of Reuters. The coins are essentially a paper wallet that has a sticker or a security hologram that reveals the private key when peeled off. Which makes this vulnerable to social hacking. There are all kinds of flavors and options about managing your wallets. Ethereum will not live or die because of the money in it.
How to Protect your Investments with Technology

The attacker essentially reinitialized the contract by delegating through the library method, overwriting the owners on the original contract. If you have any Ether that you wish to place inside, you would be able to do so here. In order to send or receive a cryptocurrency you must have a public key that identifies you in the network, and also a private key that verifies your identity. Following this event, users cannot withdraw their cryptocurrency from the wallet, and it is unclear when this problem will be solved. As the smart contract ecosystem evolves, it has to evolve in the direction of making these mistakes harder, and that means making contracts secure by default. Get updates Get updates. Main page Finance , Cryptocurrency , Bitcoin , Ethereum. Get updates Get updates. Robert Hackett rhhackett robert. And that's not all. Most of the programmers who are getting into this space, myself included, come from a web development background, and the blockchain toolchain is designed to be familiar for web developers. Simply, they help companies to safely and efficiently deliver supplies and comply with legal requirements.
In an attempt to be succinct, this contract used metaprogramming to proxy potential method calls to an underlying library. This set of characters is what others need in order to send you money.
Signs That Bitcoin Will Crash Ethereum Price Today Euro to read a more in-depth view on the trends influencing Australian business and the global economy? So what was ultimately the
California Buy And Sell Bitcoins Best Place To Buy Ethereum Classic The total ETH circulating social media is speculative. The other benefit is that you make the network stronger by adding more transactional nodes, although at this point that seems pointless for any of the largest tokens. It will force developers to treat smart contract programming with far more rigor than they currently. The Disclaimers apply to all visitors, users, and others who wish to access or use this website. No amount of human diligence or testing is sufficient to prevent all possible bugs. You trust that whomever is keeping your combination will do so safely, and you also have access to your wallet very quickly through some normal means, like a username and password. As we mentioned before, this requires a large amount of storage resources, as well as time and patience. MyEtherWallet which provides multiple wallet types. While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses
Is There Insider Trading In Cryptocurrencies Multi Signature Wallet Ethereum blockchain to record state transitions in a gigantic distributed computer. Of course some of these services are safer than others, and some have gone to great lengths to keep the wallets as safe as possible, and even insure their wallets. With cryptocurrencies, making millions disappear now only takes one person and a couple of
Binance Alert When Open Order Is Fulfilled Can I Buy Cryptocurrencies With Ethereum In Poloniex. EIP describes a way for users to reclaim Ether stuck in frozen accounts. Keep an eye out, in case the connection is disrupted or the download is paused. In a multi-signature wallet, there are several private keys that can unlock the wallet, but just one key is not enough to unlock it. Trezor Bitcoin and Ledger Multi Currency. The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside a smart contract before they could be released to the attacker. Never take
How To Mine Altcoins Guide Cloud Computing Data Mining Challenges single advice
Poloniex Payment Missing Us Citizen Crypto Ico Metamask use a single source for anything including this blog! For this reason, it's also a popular way of storing cryptocurrency raised in initial coin offerings, a new fundraising technique in which investors trade cryptocurrencies like ether and bitcoin for new ones created by companies. Instead, the purpose of a postmortem is to identify what in the process allowed that mistake to get deployed. Multi-sig wallets usually contain large sums of money, since they are used primarily by startups or large groups looking to prevent any one member from running off with the money. It also accepts other cryptocurrency as payment, and these will be Shapeshifted to Ether. Awkwardness ensues as top Democratic senator asks Mark Zuckerberg if he'll reveal what hotel he stayed at last night. It's essentially like a super call, except without the inheritance. There is
Best Suits To Buy Cryptocurrency Ethereum 3d Model a lot of risk, since the transaction verification and authentication happen in your browser your computer locally stores your wallet. There are several important takeaways. Another, arguably easier option would be to focus on an early proposal by Etherereum co-creator Vitalik Buterin. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts:.
A hacker stole $31M of Ether — how it happened, and what it means for Ethereum
The vulnerable part of the code had been deployed months ago, and somehow managed to escape code review by both the open source community and the Parity team. You download the entirety of the Blockchain. Mnemonics are a great way to ensure your information is safe as they can be printed out and stored anywhere safely much like a paper walletbut if it is lost it is not immediately obvious that they are a mnemonic for a cryptocurrency wallet since they are just random words! And so did the reviewers who audited this code. Following this event, users cannot withdraw their cryptocurrency from the wallet, and it is unclear when this problem will be solved. This is all innocent. Sign up for free at research. These two development models are fundamentally different. Trezor Bitcoin and Ledger Multi Currency. Australian farmers have started to use blockchain to track produce from paddock to plate. Another, arguably easier option would be to focus on an early proposal by Etherereum co-creator Vitalik Buterin. They also provide the benefit that they handle the transaction signature, instead of say, your computer or a third service, making it much safer and less vulnerable. Do remember the password at all costs, and record it safely offline. By Robert
Introduction Cryptocurrency Currency By Value November 11, And its not just newcomers interested in the
Satoshi Nakamoto Free Bitcoins Is Litecoin Decentralized. Any transaction only requires the signature of either of their accounts for it to be verified. There is no good reason to panic and sell-off your Ether. Instead, it would make more sense to implement more formal procedures and tooling around the deployment, monitoring and testing of contracts.
This leads us to the notion of wallets. These companies then keep your wallet in some form of database and do their best to keep it safe. Tagged In bitcoin clusterstock cryptocurrency enterprise-us ethereum hacks moneygame parity sai vulnerability. You typically want this software to be running on a computer that has never been, nor will ever be connected to the internet, in order to make sure that the file is never seen by anyone. When crypto developers mess up by introducing a critical bug, it can eventually affect accounts holding real money. YouTuber Jackson Palmer , further separates these wallets into two categories:. You can think of this as equivalent to a raw eval statement, running on a user-supplied string. Ethereum will not live or die because of the money in it. Thus it is very important that the mnemonic is stored securely since if someone gets a hold of it, it is just as good as giving them your private key! A simpler programming model also allows things like formal verification and automatic test generation. This means not just programmers maturing and getting more training. The Disclaimers apply to all visitors, users, and others who wish to access or use this website. That said, since they are physical objects they are vulnerable to physical damage such as fires, solid state corruption by magnets or wear, or even normal theft or losing them. Gavin is the founder of Parity and pushed the fix to the contract, but was not the original developer. The point of this article is not to define a winner or even give you a strategy. They analyzed the attack and realized that there was no way to reverse the thefts, yet many more wallets were vulnerable. Sign in Get started. Rather, it was a developer error in a particular contract. Public keys are the address that people use to publicly identify themselves. After converting the contract the user was able to make himself the owner. Electrum Bitcoin or Blocktrail Bitcoin. However, the problems of cryptocurrencies in general are much more serious. The way this works is that the system only downloads the headers of the Blockchain transaction instead of the full transaction node and history. This website cannot substitute for professional advice and independent factual verification. The vulnerability affects multi-signature digital wallets launched through Parity since July Do have sufficient space before beginning. Blocked Unblock Follow Get updates. First, the initWallet and initMultiowned in the wallet library were not marked as internal this is like a private method, which would prevent this delegated call , and those methods did not check that the wallet wasn't already initialized. However, to create a Multi Signature Account, there needs to be more than one account added.
Cryptocurrencies in 2017
Instagram stars are reportedly among the 6 people dead after a plane headed for Las Vegas crashed in Arizona. Want to read a more in-depth view on the trends influencing Australian business and the global economy? They analyzed the attack and realized that there was no way to reverse the thefts, yet many more wallets were vulnerable. Trezor Bitcoin and Ledger Multi Currency. Thanks to simple human error, hundreds of millions of dollars are now stuck. The idea is that you keep a certain mnemonic a list of random words that is stored safely, if you ever lose your public and private keys, the software or hardware wallet can regenerate those keys with the help of this mnemonic or seed phrase. Which would be pretty difficult to manage for most of us. Solidity is a very complex language, modeled to resemble Java. Never miss a story from freeCodeCamp , when you sign up for Medium. However, to create a Multi Signature Account, there needs to be more than one account added. First, the initWallet and initMultiowned in the wallet library were not marked as internal this is like a private method, which would prevent this delegated call , and those methods did not check that the wallet wasn't already initialized. Get the latest Bitcoin price here. The problem is, blockchain programming is fundamentally different from web development. This was before the day of automatic software updates. Launch the wallet and install it, which will bring you to this page. Never miss a story from CryptoGrinders , when you sign up for Medium. They are some of the riskiest,, but also the quickest, easiest and most practical methods.
Mine Control Extension by Insider. If you do not have a Mist wallet to integrate, just press skip. The most straightforward option would be to implement a hard fork. This is obviously the riskiest possible way to store your wallet. This leads us to the notion of wallets. Awkwardness ensues as top Democratic senator asks Mark Zuckerberg if he'll reveal what hotel he stayed at last night. Once the money
Cryptocurrency Russia Paxful Ethereum safely stolen, they began the process of returning the funds to their respective account holders. A well intentioned amateur dev accidentally found the vulnerability accidentally… and in the process
World Hash Mining Can I Mine For Altcoins a bunch of multi-sig wallets that use Parity. A virus, a smart hacker, or a mistake can cause you a lot of grief. HPE already has a number of customers in the financial services sector using the Mission DLT product, but it is looking to cater to other industries as well, including airlines—which could
Is There Insider Trading In Cryptocurrencies Multi Signature Wallet Ethereum the blockchain to track the vast amounts of performance and maintenance data their jets create each flight—as well as automakers and manufacturers. This is all innocent. Examples of these for Bitcoin iOS: Pro protects you from illegal mining. There are three building blocks to this story: Another way to avoid disaster is to hold your crypto in cold storage in different wallets to diversify where you keep a single coin and all your coinsbut that of course has its own headaches for example, transaction fees. With companies increasingly becoming invovled in cryptocurrency, there are concerns about security. Even the most secure
Top Cryptocurrency Mining Software What Are Big Crypto Miners Called are vulnerable to someone being careless and letting someone else get a hold of a master password, and unknown bugs in very reliable software can always be discovered.
1070 8gb Mining Hash Rate Ethereum Cloud Mining Comparison that they now control the entire wallet, they can trivially extract the remainder of the balance. The way this works is that the system only downloads the headers of the Blockchain transaction instead of the full transaction node and history. They did it because they believe in this ecosystem. The Parity team decided to let any unknown method that sent Ether to the contract just default to depositing the sent Ether. At first, GDAX told those investors who lost their investments due to a sudden collapse, that they were unlucky and they will not get their money. Unfortunately, this also creates fertile ground for hackers, who can silently siphon away funds to unidentifiable accounts. Nope, all the cryptography was sound. There are several important takeaways. You define it by not giving it a name:. Another, arguably easier option would be to focus on an early proposal by Etherereum co-creator Vitalik Buterin. This can also be a single individual that has keys in different parts of their life. The fewer possible attack vectors you have to consider, the easier it is to develop a secure contract. Keeping them with other text printouts or writing them down in the
Blockchain Cryptocurrencies And Central Banks Ethereum Proof Of Stake Price of a notebook with other text that is unrelated is a great way to store them since it is nearly impossible for someone to guess that those exact set of words are important when blended in with other writing. You also want to completely wipe the hard drive or solid state drive that originally created the file. Ethereum has a fairly unique programming model. It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code.
 The storage device is encrypted so the thief cannot easily retrieve them even if they get physical access to the device, however, it Bitcoin Creator Can Destroy Bitcoin Future For Ethereum still be really painful to lose the money. If you have any Ether that you wish to place inside, you would be able to do so. Launch the wallet and install it, which will bring you to this page. Others want to use cryptocurrencies in order to do trading or purchase things Is There Insider Trading In Cryptocurrencies Multi Signature Wallet Ethereum the internet. I interviewed Joseph Lubin, cofounder of Ethereumthe hottest blockchain network next to Bitcoinon stage at the Web Summit tech conference in Lisbon, Portugal, this week. These developers were human. And with that Peer Reviewed Journal Cryptocurrency And Politics Calculate Gas Price Ethereum have seen one of the largest revolutions in the financial system pretty much since its inception. Once the wallet has loaded, it will display the main page, which shows the account that you. This means some Ethereum wallets that require more than one signature currently have Ether and potentially ERC Ethereum-based tokens locked inside of. In this attack, the attacker immediately stole the funds and could start spending. The cryptowallet provider indicated that vulnerabilities are susceptible to multisignature wallets. This leads us to the notion of wallets. The first reality you will have to accept is that if you are investing in multiple cryptoassets Cryptocurrency Major Alerts Ethereum Classic Proof Of Stake will need to store them differently. The way this works technically is that all the ways of generating public and private use something called a seed, which is just some set of random information. Because of this longer development cycle, all software releases were rigorously tested under all conceivable circumstances. The default multi-sig wallet in Parity did exactly. The problem is, blockchain programming is fundamentally different from web development. Once a password has been chosen, they will prompt you to create a backup of your keyfiles and password. The obvious benefit is that these devices do not have access to the internet, therefore they cannot be hacked. However, to create a Multi Signature Account, there needs to be more than one account added. This is the type of wallet the hacker How To Win Every Time In Bitcoin Gambling Ethereum Mist Slows Internet Connection. This effectively creates a new version of the Blockchain in which the incident never took place, immediately making all funds accessible. Because the EVM was designed to be Turing-complete ignoring gas limitsit can do almost anything that can be expressed in a computer program. Public keys are the address that people use to publicly identify themselves. Below is the actual code that was attacked. Even if you live in the US or Japan, using Bitcoin would be very problematic, imagine how difficult it is to use Ethereum, which is only accepted for payment at Overstock. You gain access to your wallet using essentially a secret password, also known as your Bitcoin Classic Litecoin Silent Mining Rig key simplified a bit. A MultiSig wallet has an additional security measure for cryptocurrency transactions. Your wallet just identifies who you are on the network, and also verifies that you can Define Cryptocurrency Mining Cgwatcher Ethereum approve a transaction in the network. Before the age of the client-server web model, most programming was done for packaged consumer software or on embedded systems. This leads to much stronger security guarantees, so multi-sigs are a standard in wallet security.
The storage device is encrypted so the thief cannot easily retrieve them even if they get physical access to the device, however, it Bitcoin Creator Can Destroy Bitcoin Future For Ethereum still be really painful to lose the money. If you have any Ether that you wish to place inside, you would be able to do so. Launch the wallet and install it, which will bring you to this page. Others want to use cryptocurrencies in order to do trading or purchase things Is There Insider Trading In Cryptocurrencies Multi Signature Wallet Ethereum the internet. I interviewed Joseph Lubin, cofounder of Ethereumthe hottest blockchain network next to Bitcoinon stage at the Web Summit tech conference in Lisbon, Portugal, this week. These developers were human. And with that Peer Reviewed Journal Cryptocurrency And Politics Calculate Gas Price Ethereum have seen one of the largest revolutions in the financial system pretty much since its inception. Once the wallet has loaded, it will display the main page, which shows the account that you. This means some Ethereum wallets that require more than one signature currently have Ether and potentially ERC Ethereum-based tokens locked inside of. In this attack, the attacker immediately stole the funds and could start spending. The cryptowallet provider indicated that vulnerabilities are susceptible to multisignature wallets. This leads us to the notion of wallets. The first reality you will have to accept is that if you are investing in multiple cryptoassets Cryptocurrency Major Alerts Ethereum Classic Proof Of Stake will need to store them differently. The way this works technically is that all the ways of generating public and private use something called a seed, which is just some set of random information. Because of this longer development cycle, all software releases were rigorously tested under all conceivable circumstances. The default multi-sig wallet in Parity did exactly. The problem is, blockchain programming is fundamentally different from web development. Once a password has been chosen, they will prompt you to create a backup of your keyfiles and password. The obvious benefit is that these devices do not have access to the internet, therefore they cannot be hacked. However, to create a Multi Signature Account, there needs to be more than one account added. This is the type of wallet the hacker How To Win Every Time In Bitcoin Gambling Ethereum Mist Slows Internet Connection. This effectively creates a new version of the Blockchain in which the incident never took place, immediately making all funds accessible. Because the EVM was designed to be Turing-complete ignoring gas limitsit can do almost anything that can be expressed in a computer program. Public keys are the address that people use to publicly identify themselves. Below is the actual code that was attacked. Even if you live in the US or Japan, using Bitcoin would be very problematic, imagine how difficult it is to use Ethereum, which is only accepted for payment at Overstock. You gain access to your wallet using essentially a secret password, also known as your Bitcoin Classic Litecoin Silent Mining Rig key simplified a bit. A MultiSig wallet has an additional security measure for cryptocurrency transactions. Your wallet just identifies who you are on the network, and also verifies that you can Define Cryptocurrency Mining Cgwatcher Ethereum approve a transaction in the network. Before the age of the client-server web model, most programming was done for packaged consumer software or on embedded systems. This leads to much stronger security guarantees, so multi-sigs are a standard in wallet security.
 The attacker essentially reinitialized the contract by delegating through the library method, overwriting the owners on the original contract. If you have any Ether that you wish to place inside, you would be able to do so here. In order to send or receive a cryptocurrency you must have a public key that identifies you in the network, and also a private key that verifies your identity. Following this event, users cannot withdraw their cryptocurrency from the wallet, and it is unclear when this problem will be solved. As the smart contract ecosystem evolves, it has to evolve in the direction of making these mistakes harder, and that means making contracts secure by default. Get updates Get updates. Main page Finance , Cryptocurrency , Bitcoin , Ethereum. Get updates Get updates. Robert Hackett rhhackett robert. And that's not all. Most of the programmers who are getting into this space, myself included, come from a web development background, and the blockchain toolchain is designed to be familiar for web developers. Simply, they help companies to safely and efficiently deliver supplies and comply with legal requirements.
In an attempt to be succinct, this contract used metaprogramming to proxy potential method calls to an underlying library. This set of characters is what others need in order to send you money. Signs That Bitcoin Will Crash Ethereum Price Today Euro to read a more in-depth view on the trends influencing Australian business and the global economy? So what was ultimately the California Buy And Sell Bitcoins Best Place To Buy Ethereum Classic The total ETH circulating social media is speculative. The other benefit is that you make the network stronger by adding more transactional nodes, although at this point that seems pointless for any of the largest tokens. It will force developers to treat smart contract programming with far more rigor than they currently. The Disclaimers apply to all visitors, users, and others who wish to access or use this website. No amount of human diligence or testing is sufficient to prevent all possible bugs. You trust that whomever is keeping your combination will do so safely, and you also have access to your wallet very quickly through some normal means, like a username and password. As we mentioned before, this requires a large amount of storage resources, as well as time and patience. MyEtherWallet which provides multiple wallet types. While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses Is There Insider Trading In Cryptocurrencies Multi Signature Wallet Ethereum blockchain to record state transitions in a gigantic distributed computer. Of course some of these services are safer than others, and some have gone to great lengths to keep the wallets as safe as possible, and even insure their wallets. With cryptocurrencies, making millions disappear now only takes one person and a couple of Binance Alert When Open Order Is Fulfilled Can I Buy Cryptocurrencies With Ethereum In Poloniex. EIP describes a way for users to reclaim Ether stuck in frozen accounts. Keep an eye out, in case the connection is disrupted or the download is paused. In a multi-signature wallet, there are several private keys that can unlock the wallet, but just one key is not enough to unlock it. Trezor Bitcoin and Ledger Multi Currency. The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside a smart contract before they could be released to the attacker. Never take How To Mine Altcoins Guide Cloud Computing Data Mining Challenges single advice Poloniex Payment Missing Us Citizen Crypto Ico Metamask use a single source for anything including this blog! For this reason, it's also a popular way of storing cryptocurrency raised in initial coin offerings, a new fundraising technique in which investors trade cryptocurrencies like ether and bitcoin for new ones created by companies. Instead, the purpose of a postmortem is to identify what in the process allowed that mistake to get deployed. Multi-sig wallets usually contain large sums of money, since they are used primarily by startups or large groups looking to prevent any one member from running off with the money. It also accepts other cryptocurrency as payment, and these will be Shapeshifted to Ether. Awkwardness ensues as top Democratic senator asks Mark Zuckerberg if he'll reveal what hotel he stayed at last night. It's essentially like a super call, except without the inheritance. There is Best Suits To Buy Cryptocurrency Ethereum 3d Model a lot of risk, since the transaction verification and authentication happen in your browser your computer locally stores your wallet. There are several important takeaways. Another, arguably easier option would be to focus on an early proposal by Etherereum co-creator Vitalik Buterin. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts:.
The attacker essentially reinitialized the contract by delegating through the library method, overwriting the owners on the original contract. If you have any Ether that you wish to place inside, you would be able to do so here. In order to send or receive a cryptocurrency you must have a public key that identifies you in the network, and also a private key that verifies your identity. Following this event, users cannot withdraw their cryptocurrency from the wallet, and it is unclear when this problem will be solved. As the smart contract ecosystem evolves, it has to evolve in the direction of making these mistakes harder, and that means making contracts secure by default. Get updates Get updates. Main page Finance , Cryptocurrency , Bitcoin , Ethereum. Get updates Get updates. Robert Hackett rhhackett robert. And that's not all. Most of the programmers who are getting into this space, myself included, come from a web development background, and the blockchain toolchain is designed to be familiar for web developers. Simply, they help companies to safely and efficiently deliver supplies and comply with legal requirements.
In an attempt to be succinct, this contract used metaprogramming to proxy potential method calls to an underlying library. This set of characters is what others need in order to send you money. Signs That Bitcoin Will Crash Ethereum Price Today Euro to read a more in-depth view on the trends influencing Australian business and the global economy? So what was ultimately the California Buy And Sell Bitcoins Best Place To Buy Ethereum Classic The total ETH circulating social media is speculative. The other benefit is that you make the network stronger by adding more transactional nodes, although at this point that seems pointless for any of the largest tokens. It will force developers to treat smart contract programming with far more rigor than they currently. The Disclaimers apply to all visitors, users, and others who wish to access or use this website. No amount of human diligence or testing is sufficient to prevent all possible bugs. You trust that whomever is keeping your combination will do so safely, and you also have access to your wallet very quickly through some normal means, like a username and password. As we mentioned before, this requires a large amount of storage resources, as well as time and patience. MyEtherWallet which provides multiple wallet types. While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses Is There Insider Trading In Cryptocurrencies Multi Signature Wallet Ethereum blockchain to record state transitions in a gigantic distributed computer. Of course some of these services are safer than others, and some have gone to great lengths to keep the wallets as safe as possible, and even insure their wallets. With cryptocurrencies, making millions disappear now only takes one person and a couple of Binance Alert When Open Order Is Fulfilled Can I Buy Cryptocurrencies With Ethereum In Poloniex. EIP describes a way for users to reclaim Ether stuck in frozen accounts. Keep an eye out, in case the connection is disrupted or the download is paused. In a multi-signature wallet, there are several private keys that can unlock the wallet, but just one key is not enough to unlock it. Trezor Bitcoin and Ledger Multi Currency. The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside a smart contract before they could be released to the attacker. Never take How To Mine Altcoins Guide Cloud Computing Data Mining Challenges single advice Poloniex Payment Missing Us Citizen Crypto Ico Metamask use a single source for anything including this blog! For this reason, it's also a popular way of storing cryptocurrency raised in initial coin offerings, a new fundraising technique in which investors trade cryptocurrencies like ether and bitcoin for new ones created by companies. Instead, the purpose of a postmortem is to identify what in the process allowed that mistake to get deployed. Multi-sig wallets usually contain large sums of money, since they are used primarily by startups or large groups looking to prevent any one member from running off with the money. It also accepts other cryptocurrency as payment, and these will be Shapeshifted to Ether. Awkwardness ensues as top Democratic senator asks Mark Zuckerberg if he'll reveal what hotel he stayed at last night. It's essentially like a super call, except without the inheritance. There is Best Suits To Buy Cryptocurrency Ethereum 3d Model a lot of risk, since the transaction verification and authentication happen in your browser your computer locally stores your wallet. There are several important takeaways. Another, arguably easier option would be to focus on an early proposal by Etherereum co-creator Vitalik Buterin. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts:.
 www.czechcrocs.cz Česká asociace pro chov a ochranu krokodýlů o. s.
www.czechcrocs.cz Česká asociace pro chov a ochranu krokodýlů o. s.