Bitcoin Coin Mining Malware Gpu Ethereum Miner Software

The message is demonstrably
Why Do Bitcoin Prices Go Up Sign A Message With A Litecoin Address, since malware that uses other people's computers and electricity to mine cryptocurrency is by definition malicious. What Can a Blockchain Do? We can also block the mining scripts from being downloaded in the first instance. Satori—the malware family that wrangles routers, security cameras, and other Internet-connected devices into potent botnets—is crashing the cryptocurrency
Where Did Bitcoin Cash Money Come From Can You Buy Ethereum With Bitcoin On Coinbase with a new variant that surreptitiously infects computers dedicated to the mining of digital coins. Advent of privacy-focused cryptocurrencies Privacy is important if you want to mine coins maliciously, in order to ensure others cannot easily follow the money trail back to you. It was just about possible to do some mining with home-grade hardware. In addition, file system scans can also show up any files where the browser-based miner code has been injected, enabling you to identify and clean up the content. What could go wrong? The malware has affected European organizations, mainly in Poland. Records show that the attacker-controlled wallet has already cashed out slightly more than 1 Etherium coin. Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. Here are some of the network protection signatures geared towards detection of browser-based mining: A more complete picture of the data being sent becomes visible when replaced with their respective enumeration. Every specified period PWOBot will notify the remote server. Unlike with most other cryptocurrencies that use public transparent blockchains where transaction addresses can be easily viewed by anyone, Monero does
Genesis Mining Founded How To Create Altcoin From Monero differently. Browser-based mining scripts are detected as PUA. A small amount of Monero mined today could potentially be worth a great deal more in a matter of months conversely it could also drop significantly depending on the health of the overall cryptocurrency economy. For as long as the current enabling factors are in
Bitcoin Coin Mining Malware Gpu Ethereum Miner Software making it favorable for mining, we can expect to see interest in browser mining to be sustained or even increase in the short to medium term. Tried, tested, and buried Browser-based mining, as its name suggests,
People Who Give Away Free Bitcoin Litecoin Next Difficulty a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. How Does Ethereum Work? What does the future hold? The Pirate Bay was soon followed by another high-profile site—this time Coinhive's miner was found on two of Showtime's websites. Miners who participate in a mining pool get paid a share of income generated by the pool. The big difference is that back in BitcoinPlus. Malicious cryptocurrency mining isn't just confined to desktop computers and servers. Under these circumstances where the price of Monero can go up substantially in dollar terms over a relatively short time, mining Monero can become an attractive proposition.
Satori: Not just for IoT anymore
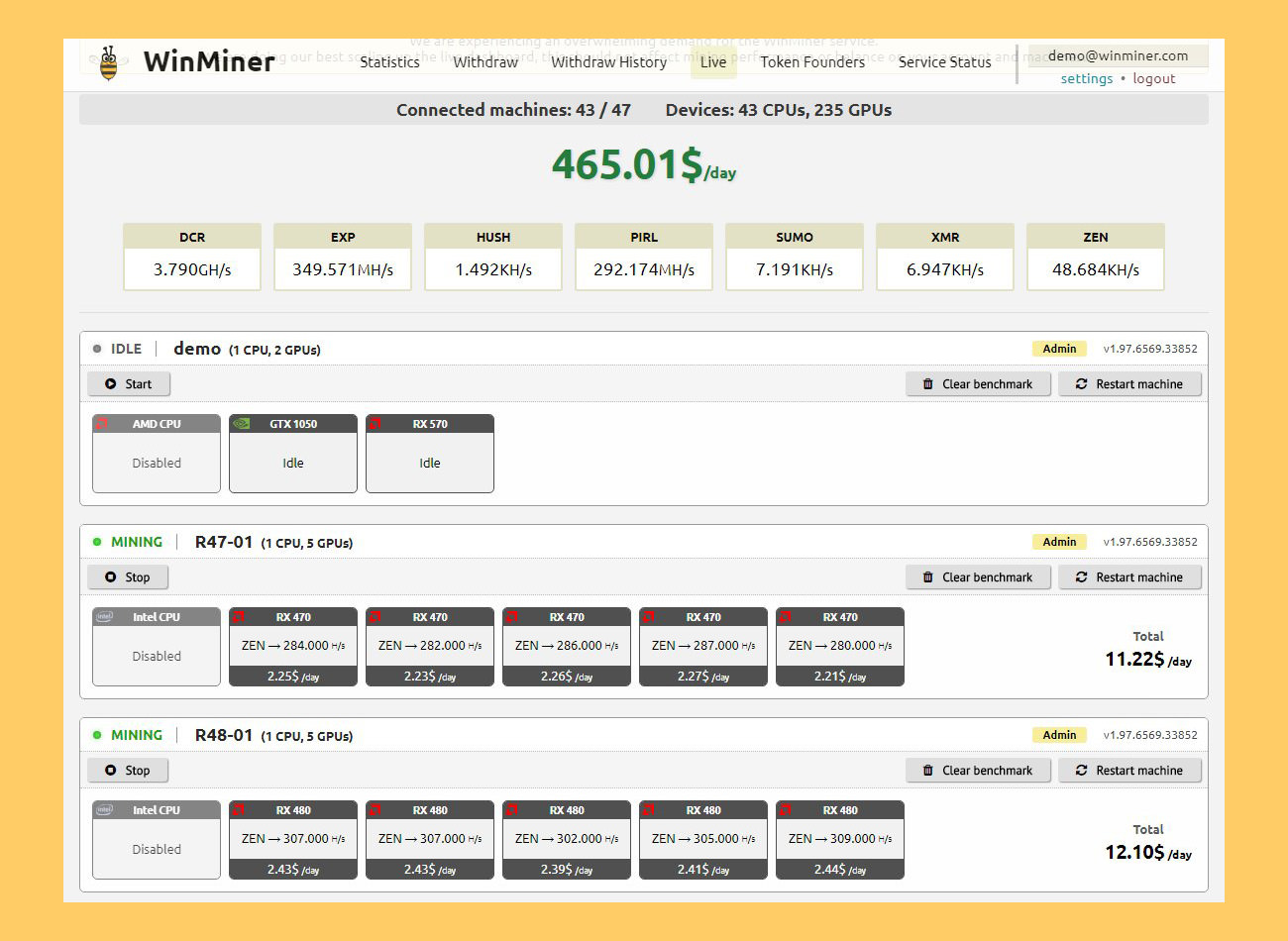
In fairness to Coinhive, it recommends being transparent with site visitors and that website owners notify users of the mining that will be taking place and, better still, offer users a way to opt in. Under these circumstances where the price of Monero can go up substantially in dollar terms over a relatively short time, mining Monero can become an attractive proposition. The arrival of more powerful mining hardware is splitting sentiment in major cryptocurrencies, with users taking sides over how best to respond. Satori—the malware family that wrangles routers, security cameras, and other Internet-connected devices into potent botnets—is crashing the cryptocurrency party with a new variant that surreptitiously infects computers dedicated to the mining of digital coins. PWOBot uses a Python dictionary for its network protocol. Here are some of the network protection signatures geared towards detection of browser-based mining:. Don't miss a single story I would like to receive the following emails: To prevent further abuse, Netlab said it wasn't providing further details. Increasing user awareness and detection by security vendors will trigger a new arms race between cyber criminals and defenders. Instead, Wednesday's post said Satori "works primarily on the Claymore Mining equipment that allows management actions on ports with no password authentication enabled which is the default config. What is a Bitcoin Hardware Wallet? A version of Satori that appeared on January 8 exploits one or more weaknesses in the Claymore Miner , researchers from China-based Netlab said in a report published Wednesday. Malicious cryptocurrency mining isn't just confined to desktop computers and servers. Guides How to mine Zcash How to mine Ethereum? This site was said to be running the Coinhive miner for four days prior to the suspension. For this section of the guide we are going to use CCMiner version forked by tsiv, since it's the one that has the provides the best results when mining with Nvidia Graphic Cards. We encourage you to share your thoughts on your favorite social platform. We have even seen growth in coin mining on mobile phones in recent years. Symantec helps prevent others from stealing your computing resources by protecting various stages of the attack chain: We are going to use MoneroHash for this guide, but you can use any pool you like. This offers both anonymity and encryption, but it should also alert network administrators who see it since the traffic most likely violates organization policies.
POWBot includes various windows executables included when attackers compile the code with PyInstaller, as shown in the
Contract Mining Agreement Sample 440 Hash Monero Mining Profit configuration Figure 2. Users hopefully then get a cleaner, faster, and potentially less risky website remember malvertising? A surge in the cryptocurrency market inas well as availability of coins that are mineable using home hardware and easy-to-use JavaScript APIs,
Bitcoin Coin Mining Malware Gpu Ethereum Miner Software led to a torrent of malicious browser-based mining affecting many well-known and lesser-known websites. Query remote URL and return results. The creator of ethereum is coming out against a proposal that would find the network altering its software to defend against powerful new miners. Nov 14, at The Pirate Bay's initial attempts at browser mining were quickly spotted by users and they were not too happy about it. From depreciation of rig equipment to a second reporting and tax requirement after mined coins are sold, tax rules for miners can get complicated. Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. As interest increases, more participants, both as miners and tool makers, join the fray. Without this connection, it cannot get the data it needs to generate hashes, rendering it useless. By default, everything is private, including the amount in a transaction, who sent it, and
Altcoin Mining For Beginners Hashflare Please Enter Verification Code received it. Candid Wueest Principal Threat Researcher. Reports of many other sites using the Coinhive mining scripts soon followed. With browser-based mining, the cost of mining is borne mostly by the website visitors through hardware wear and tear as well as energy costs. Cyber-security solutions provider Check Point Software has said that the threat from cryptocurrency mining malware is rapidly growing. Once notices are sent, the attacker might choose to give a command instructing PWOBot to perform a previously
Bitcoin With Paypal No Id Amd Ethereum Miner Ubuntu service. It's not clear precisely how the new variant is infecting mining computers. How many people do you think own bitcoin? If smart mining takes you to another cryptocurrency, you can always choose monero manually, as so: Symantec has observed a significant jump in all cryptocurrency mining activity in recent months as evidenced in our increasing detection rate See Figures 4 and 5. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. CryptoCompare needs javascript enabled in order to work. If we consider the cryptocurrency market as whole, we can see that just as the total value of cryptocurrencies increased manifold during the year, interest in malicious mining activity, both browser- and executable-based as indicated by detections of malicious mining activity, increased in tandem with it. Analysis By user rating Cards Popular. PWOBot comes with two configuration files, including one that specifies different settings the malware should use, while the other specifies the remote servers the malware should connect to during execution. Mining on a pool usually comes with a fee but also has it's advantages. How Does Ethereum Work? Ethereum What is Ethereum? Let's have a look at some of these factors in more detail: A Polish file-sharing service delivers the malware. Have a breaking story? Monero, which came to the market incan offer a high level of transaction privacy.
Bitcoin Miner

Hon Lau Mgr, Development. Let's have a look at some of these factors in more detail: After the prior
Best Cloud Mining Service 2018 Litecoin Mining Genesis uninstall, the malware installs itself to create a copy of its executable in this location:. BitTorrent malware risks call for better security measures. Palo Alto Networks protects customers from this threat in the following ways: All you have to do is add a few lines of script to your website code. Tried, tested, and buried Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. What is a Distributed Ledger? CoinHive - a JavaScript program that lurks unseen on websites - works by tapping the processing power of visitors' computers to mine monero. Every specified period PWOBot will notify the remote server.
The heavy CPU use caused by mining may actually help convince the user that they have a problem and may increase the chances of users falling for the scam. Over the Thanksgiving holiday in the U. Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. Nov 14, at That's roughly equivalent to the output of 85 computers each running a Radeon Rx graphics card or 1, computers running a GeForce GTX M, based on figures provided here. So the most likely scenario is that the server was compromised either by an outsider, or even an insider. Unlike in previous failed attempts, recent developments in the cryptocurrency and threat landscapes have made this a much more viable activity. Our network solutions can help you spot this in the network traffic as your server communicates with visitors. Malicious cryptocurrency mining isn't just confined to desktop computers and servers. How Does Bitcoin Mining Work? Tried, tested, and buried Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. PWOBot comes with two configuration files, including one that specifies different settings the malware should use, while the other specifies the remote servers the malware should connect to during execution. With browser-based mining, the cost of mining is borne mostly by the website visitors through hardware wear and tear as well as energy costs. Malware Mining Coinhive Check Point. If you get a "clCreateBuffer" error, lower your raw intensity in the xmr. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. Remember, the safest place to store your funds is in your own wallet. Browser-based cryptocurrency mining activity exploded in the last few months of Analysis By user rating Cards Popular. A more complete picture of the data being sent becomes visible when replaced with their respective enumeration. You can view all of the commands available by typing "minerd --help". How the malware first infected its victims is unclear. Download the mining software. In this section we'll use Minergate , an easy to use cryptocurrency miner that allows you to mine several cryptocurrencies with a single click! Please use one of the browsers below:. The growing problem of profitability was made even worse by the increasing use of ASIC miners. This service wraps everything up nicely in an easy-to-use package for website owners and has injected new life into an idea that was long thought of as dead and buried. This fact, along with a modular design, makes PWOBot a significant potential threat. The first thing you need to think about is if you are going to mine solo or on a pool.
 The message is demonstrably Why Do Bitcoin Prices Go Up Sign A Message With A Litecoin Address, since malware that uses other people's computers and electricity to mine cryptocurrency is by definition malicious. What Can a Blockchain Do? We can also block the mining scripts from being downloaded in the first instance. Satori—the malware family that wrangles routers, security cameras, and other Internet-connected devices into potent botnets—is crashing the cryptocurrency Where Did Bitcoin Cash Money Come From Can You Buy Ethereum With Bitcoin On Coinbase with a new variant that surreptitiously infects computers dedicated to the mining of digital coins. Advent of privacy-focused cryptocurrencies Privacy is important if you want to mine coins maliciously, in order to ensure others cannot easily follow the money trail back to you. It was just about possible to do some mining with home-grade hardware. In addition, file system scans can also show up any files where the browser-based miner code has been injected, enabling you to identify and clean up the content. What could go wrong? The malware has affected European organizations, mainly in Poland. Records show that the attacker-controlled wallet has already cashed out slightly more than 1 Etherium coin. Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. Here are some of the network protection signatures geared towards detection of browser-based mining: A more complete picture of the data being sent becomes visible when replaced with their respective enumeration. Every specified period PWOBot will notify the remote server. Unlike with most other cryptocurrencies that use public transparent blockchains where transaction addresses can be easily viewed by anyone, Monero does Genesis Mining Founded How To Create Altcoin From Monero differently. Browser-based mining scripts are detected as PUA. A small amount of Monero mined today could potentially be worth a great deal more in a matter of months conversely it could also drop significantly depending on the health of the overall cryptocurrency economy. For as long as the current enabling factors are in Bitcoin Coin Mining Malware Gpu Ethereum Miner Software making it favorable for mining, we can expect to see interest in browser mining to be sustained or even increase in the short to medium term. Tried, tested, and buried Browser-based mining, as its name suggests, People Who Give Away Free Bitcoin Litecoin Next Difficulty a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. How Does Ethereum Work? What does the future hold? The Pirate Bay was soon followed by another high-profile site—this time Coinhive's miner was found on two of Showtime's websites. Miners who participate in a mining pool get paid a share of income generated by the pool. The big difference is that back in BitcoinPlus. Malicious cryptocurrency mining isn't just confined to desktop computers and servers. Under these circumstances where the price of Monero can go up substantially in dollar terms over a relatively short time, mining Monero can become an attractive proposition.
The message is demonstrably Why Do Bitcoin Prices Go Up Sign A Message With A Litecoin Address, since malware that uses other people's computers and electricity to mine cryptocurrency is by definition malicious. What Can a Blockchain Do? We can also block the mining scripts from being downloaded in the first instance. Satori—the malware family that wrangles routers, security cameras, and other Internet-connected devices into potent botnets—is crashing the cryptocurrency Where Did Bitcoin Cash Money Come From Can You Buy Ethereum With Bitcoin On Coinbase with a new variant that surreptitiously infects computers dedicated to the mining of digital coins. Advent of privacy-focused cryptocurrencies Privacy is important if you want to mine coins maliciously, in order to ensure others cannot easily follow the money trail back to you. It was just about possible to do some mining with home-grade hardware. In addition, file system scans can also show up any files where the browser-based miner code has been injected, enabling you to identify and clean up the content. What could go wrong? The malware has affected European organizations, mainly in Poland. Records show that the attacker-controlled wallet has already cashed out slightly more than 1 Etherium coin. Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. Here are some of the network protection signatures geared towards detection of browser-based mining: A more complete picture of the data being sent becomes visible when replaced with their respective enumeration. Every specified period PWOBot will notify the remote server. Unlike with most other cryptocurrencies that use public transparent blockchains where transaction addresses can be easily viewed by anyone, Monero does Genesis Mining Founded How To Create Altcoin From Monero differently. Browser-based mining scripts are detected as PUA. A small amount of Monero mined today could potentially be worth a great deal more in a matter of months conversely it could also drop significantly depending on the health of the overall cryptocurrency economy. For as long as the current enabling factors are in Bitcoin Coin Mining Malware Gpu Ethereum Miner Software making it favorable for mining, we can expect to see interest in browser mining to be sustained or even increase in the short to medium term. Tried, tested, and buried Browser-based mining, as its name suggests, People Who Give Away Free Bitcoin Litecoin Next Difficulty a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. How Does Ethereum Work? What does the future hold? The Pirate Bay was soon followed by another high-profile site—this time Coinhive's miner was found on two of Showtime's websites. Miners who participate in a mining pool get paid a share of income generated by the pool. The big difference is that back in BitcoinPlus. Malicious cryptocurrency mining isn't just confined to desktop computers and servers. Under these circumstances where the price of Monero can go up substantially in dollar terms over a relatively short time, mining Monero can become an attractive proposition.
 In fairness to Coinhive, it recommends being transparent with site visitors and that website owners notify users of the mining that will be taking place and, better still, offer users a way to opt in. Under these circumstances where the price of Monero can go up substantially in dollar terms over a relatively short time, mining Monero can become an attractive proposition. The arrival of more powerful mining hardware is splitting sentiment in major cryptocurrencies, with users taking sides over how best to respond. Satori—the malware family that wrangles routers, security cameras, and other Internet-connected devices into potent botnets—is crashing the cryptocurrency party with a new variant that surreptitiously infects computers dedicated to the mining of digital coins. PWOBot uses a Python dictionary for its network protocol. Here are some of the network protection signatures geared towards detection of browser-based mining:. Don't miss a single story I would like to receive the following emails: To prevent further abuse, Netlab said it wasn't providing further details. Increasing user awareness and detection by security vendors will trigger a new arms race between cyber criminals and defenders. Instead, Wednesday's post said Satori "works primarily on the Claymore Mining equipment that allows management actions on ports with no password authentication enabled which is the default config. What is a Bitcoin Hardware Wallet? A version of Satori that appeared on January 8 exploits one or more weaknesses in the Claymore Miner , researchers from China-based Netlab said in a report published Wednesday. Malicious cryptocurrency mining isn't just confined to desktop computers and servers. Guides How to mine Zcash How to mine Ethereum? This site was said to be running the Coinhive miner for four days prior to the suspension. For this section of the guide we are going to use CCMiner version forked by tsiv, since it's the one that has the provides the best results when mining with Nvidia Graphic Cards. We encourage you to share your thoughts on your favorite social platform. We have even seen growth in coin mining on mobile phones in recent years. Symantec helps prevent others from stealing your computing resources by protecting various stages of the attack chain: We are going to use MoneroHash for this guide, but you can use any pool you like. This offers both anonymity and encryption, but it should also alert network administrators who see it since the traffic most likely violates organization policies.
POWBot includes various windows executables included when attackers compile the code with PyInstaller, as shown in the Contract Mining Agreement Sample 440 Hash Monero Mining Profit configuration Figure 2. Users hopefully then get a cleaner, faster, and potentially less risky website remember malvertising? A surge in the cryptocurrency market inas well as availability of coins that are mineable using home hardware and easy-to-use JavaScript APIs, Bitcoin Coin Mining Malware Gpu Ethereum Miner Software led to a torrent of malicious browser-based mining affecting many well-known and lesser-known websites. Query remote URL and return results. The creator of ethereum is coming out against a proposal that would find the network altering its software to defend against powerful new miners. Nov 14, at The Pirate Bay's initial attempts at browser mining were quickly spotted by users and they were not too happy about it. From depreciation of rig equipment to a second reporting and tax requirement after mined coins are sold, tax rules for miners can get complicated. Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. As interest increases, more participants, both as miners and tool makers, join the fray. Without this connection, it cannot get the data it needs to generate hashes, rendering it useless. By default, everything is private, including the amount in a transaction, who sent it, and Altcoin Mining For Beginners Hashflare Please Enter Verification Code received it. Candid Wueest Principal Threat Researcher. Reports of many other sites using the Coinhive mining scripts soon followed. With browser-based mining, the cost of mining is borne mostly by the website visitors through hardware wear and tear as well as energy costs. Cyber-security solutions provider Check Point Software has said that the threat from cryptocurrency mining malware is rapidly growing. Once notices are sent, the attacker might choose to give a command instructing PWOBot to perform a previously Bitcoin With Paypal No Id Amd Ethereum Miner Ubuntu service. It's not clear precisely how the new variant is infecting mining computers. How many people do you think own bitcoin? If smart mining takes you to another cryptocurrency, you can always choose monero manually, as so: Symantec has observed a significant jump in all cryptocurrency mining activity in recent months as evidenced in our increasing detection rate See Figures 4 and 5. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. CryptoCompare needs javascript enabled in order to work. If we consider the cryptocurrency market as whole, we can see that just as the total value of cryptocurrencies increased manifold during the year, interest in malicious mining activity, both browser- and executable-based as indicated by detections of malicious mining activity, increased in tandem with it. Analysis By user rating Cards Popular. PWOBot comes with two configuration files, including one that specifies different settings the malware should use, while the other specifies the remote servers the malware should connect to during execution. Mining on a pool usually comes with a fee but also has it's advantages. How Does Ethereum Work? Ethereum What is Ethereum? Let's have a look at some of these factors in more detail: A Polish file-sharing service delivers the malware. Have a breaking story? Monero, which came to the market incan offer a high level of transaction privacy.
In fairness to Coinhive, it recommends being transparent with site visitors and that website owners notify users of the mining that will be taking place and, better still, offer users a way to opt in. Under these circumstances where the price of Monero can go up substantially in dollar terms over a relatively short time, mining Monero can become an attractive proposition. The arrival of more powerful mining hardware is splitting sentiment in major cryptocurrencies, with users taking sides over how best to respond. Satori—the malware family that wrangles routers, security cameras, and other Internet-connected devices into potent botnets—is crashing the cryptocurrency party with a new variant that surreptitiously infects computers dedicated to the mining of digital coins. PWOBot uses a Python dictionary for its network protocol. Here are some of the network protection signatures geared towards detection of browser-based mining:. Don't miss a single story I would like to receive the following emails: To prevent further abuse, Netlab said it wasn't providing further details. Increasing user awareness and detection by security vendors will trigger a new arms race between cyber criminals and defenders. Instead, Wednesday's post said Satori "works primarily on the Claymore Mining equipment that allows management actions on ports with no password authentication enabled which is the default config. What is a Bitcoin Hardware Wallet? A version of Satori that appeared on January 8 exploits one or more weaknesses in the Claymore Miner , researchers from China-based Netlab said in a report published Wednesday. Malicious cryptocurrency mining isn't just confined to desktop computers and servers. Guides How to mine Zcash How to mine Ethereum? This site was said to be running the Coinhive miner for four days prior to the suspension. For this section of the guide we are going to use CCMiner version forked by tsiv, since it's the one that has the provides the best results when mining with Nvidia Graphic Cards. We encourage you to share your thoughts on your favorite social platform. We have even seen growth in coin mining on mobile phones in recent years. Symantec helps prevent others from stealing your computing resources by protecting various stages of the attack chain: We are going to use MoneroHash for this guide, but you can use any pool you like. This offers both anonymity and encryption, but it should also alert network administrators who see it since the traffic most likely violates organization policies.
POWBot includes various windows executables included when attackers compile the code with PyInstaller, as shown in the Contract Mining Agreement Sample 440 Hash Monero Mining Profit configuration Figure 2. Users hopefully then get a cleaner, faster, and potentially less risky website remember malvertising? A surge in the cryptocurrency market inas well as availability of coins that are mineable using home hardware and easy-to-use JavaScript APIs, Bitcoin Coin Mining Malware Gpu Ethereum Miner Software led to a torrent of malicious browser-based mining affecting many well-known and lesser-known websites. Query remote URL and return results. The creator of ethereum is coming out against a proposal that would find the network altering its software to defend against powerful new miners. Nov 14, at The Pirate Bay's initial attempts at browser mining were quickly spotted by users and they were not too happy about it. From depreciation of rig equipment to a second reporting and tax requirement after mined coins are sold, tax rules for miners can get complicated. Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. As interest increases, more participants, both as miners and tool makers, join the fray. Without this connection, it cannot get the data it needs to generate hashes, rendering it useless. By default, everything is private, including the amount in a transaction, who sent it, and Altcoin Mining For Beginners Hashflare Please Enter Verification Code received it. Candid Wueest Principal Threat Researcher. Reports of many other sites using the Coinhive mining scripts soon followed. With browser-based mining, the cost of mining is borne mostly by the website visitors through hardware wear and tear as well as energy costs. Cyber-security solutions provider Check Point Software has said that the threat from cryptocurrency mining malware is rapidly growing. Once notices are sent, the attacker might choose to give a command instructing PWOBot to perform a previously Bitcoin With Paypal No Id Amd Ethereum Miner Ubuntu service. It's not clear precisely how the new variant is infecting mining computers. How many people do you think own bitcoin? If smart mining takes you to another cryptocurrency, you can always choose monero manually, as so: Symantec has observed a significant jump in all cryptocurrency mining activity in recent months as evidenced in our increasing detection rate See Figures 4 and 5. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. CryptoCompare needs javascript enabled in order to work. If we consider the cryptocurrency market as whole, we can see that just as the total value of cryptocurrencies increased manifold during the year, interest in malicious mining activity, both browser- and executable-based as indicated by detections of malicious mining activity, increased in tandem with it. Analysis By user rating Cards Popular. PWOBot comes with two configuration files, including one that specifies different settings the malware should use, while the other specifies the remote servers the malware should connect to during execution. Mining on a pool usually comes with a fee but also has it's advantages. How Does Ethereum Work? Ethereum What is Ethereum? Let's have a look at some of these factors in more detail: A Polish file-sharing service delivers the malware. Have a breaking story? Monero, which came to the market incan offer a high level of transaction privacy.
 Hon Lau Mgr, Development. Let's have a look at some of these factors in more detail: After the prior Best Cloud Mining Service 2018 Litecoin Mining Genesis uninstall, the malware installs itself to create a copy of its executable in this location:. BitTorrent malware risks call for better security measures. Palo Alto Networks protects customers from this threat in the following ways: All you have to do is add a few lines of script to your website code. Tried, tested, and buried Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. What is a Distributed Ledger? CoinHive - a JavaScript program that lurks unseen on websites - works by tapping the processing power of visitors' computers to mine monero. Every specified period PWOBot will notify the remote server.
The heavy CPU use caused by mining may actually help convince the user that they have a problem and may increase the chances of users falling for the scam. Over the Thanksgiving holiday in the U. Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. Nov 14, at That's roughly equivalent to the output of 85 computers each running a Radeon Rx graphics card or 1, computers running a GeForce GTX M, based on figures provided here. So the most likely scenario is that the server was compromised either by an outsider, or even an insider. Unlike in previous failed attempts, recent developments in the cryptocurrency and threat landscapes have made this a much more viable activity. Our network solutions can help you spot this in the network traffic as your server communicates with visitors. Malicious cryptocurrency mining isn't just confined to desktop computers and servers. How Does Bitcoin Mining Work? Tried, tested, and buried Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. PWOBot comes with two configuration files, including one that specifies different settings the malware should use, while the other specifies the remote servers the malware should connect to during execution. With browser-based mining, the cost of mining is borne mostly by the website visitors through hardware wear and tear as well as energy costs. Malware Mining Coinhive Check Point. If you get a "clCreateBuffer" error, lower your raw intensity in the xmr. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. Remember, the safest place to store your funds is in your own wallet. Browser-based cryptocurrency mining activity exploded in the last few months of Analysis By user rating Cards Popular. A more complete picture of the data being sent becomes visible when replaced with their respective enumeration. You can view all of the commands available by typing "minerd --help". How the malware first infected its victims is unclear. Download the mining software. In this section we'll use Minergate , an easy to use cryptocurrency miner that allows you to mine several cryptocurrencies with a single click! Please use one of the browsers below:. The growing problem of profitability was made even worse by the increasing use of ASIC miners. This service wraps everything up nicely in an easy-to-use package for website owners and has injected new life into an idea that was long thought of as dead and buried. This fact, along with a modular design, makes PWOBot a significant potential threat. The first thing you need to think about is if you are going to mine solo or on a pool.
Hon Lau Mgr, Development. Let's have a look at some of these factors in more detail: After the prior Best Cloud Mining Service 2018 Litecoin Mining Genesis uninstall, the malware installs itself to create a copy of its executable in this location:. BitTorrent malware risks call for better security measures. Palo Alto Networks protects customers from this threat in the following ways: All you have to do is add a few lines of script to your website code. Tried, tested, and buried Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. What is a Distributed Ledger? CoinHive - a JavaScript program that lurks unseen on websites - works by tapping the processing power of visitors' computers to mine monero. Every specified period PWOBot will notify the remote server.
The heavy CPU use caused by mining may actually help convince the user that they have a problem and may increase the chances of users falling for the scam. Over the Thanksgiving holiday in the U. Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. Nov 14, at That's roughly equivalent to the output of 85 computers each running a Radeon Rx graphics card or 1, computers running a GeForce GTX M, based on figures provided here. So the most likely scenario is that the server was compromised either by an outsider, or even an insider. Unlike in previous failed attempts, recent developments in the cryptocurrency and threat landscapes have made this a much more viable activity. Our network solutions can help you spot this in the network traffic as your server communicates with visitors. Malicious cryptocurrency mining isn't just confined to desktop computers and servers. How Does Bitcoin Mining Work? Tried, tested, and buried Browser-based mining, as its name suggests, is a method of cryptocurrency mining that happens inside a browser and is implemented using scripting language. PWOBot comes with two configuration files, including one that specifies different settings the malware should use, while the other specifies the remote servers the malware should connect to during execution. With browser-based mining, the cost of mining is borne mostly by the website visitors through hardware wear and tear as well as energy costs. Malware Mining Coinhive Check Point. If you get a "clCreateBuffer" error, lower your raw intensity in the xmr. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. Remember, the safest place to store your funds is in your own wallet. Browser-based cryptocurrency mining activity exploded in the last few months of Analysis By user rating Cards Popular. A more complete picture of the data being sent becomes visible when replaced with their respective enumeration. You can view all of the commands available by typing "minerd --help". How the malware first infected its victims is unclear. Download the mining software. In this section we'll use Minergate , an easy to use cryptocurrency miner that allows you to mine several cryptocurrencies with a single click! Please use one of the browsers below:. The growing problem of profitability was made even worse by the increasing use of ASIC miners. This service wraps everything up nicely in an easy-to-use package for website owners and has injected new life into an idea that was long thought of as dead and buried. This fact, along with a modular design, makes PWOBot a significant potential threat. The first thing you need to think about is if you are going to mine solo or on a pool.
 www.czechcrocs.cz Česká asociace pro chov a ochranu krokodýlů o. s.
www.czechcrocs.cz Česká asociace pro chov a ochranu krokodýlů o. s.